5 Reasons Why Nmap Stealth Scan is Not Stealthy

Last updated: July 07, 2025
Whenever we use Nmap stealth scan -sS, we think that it’s stealthy, and no one can identify us that we have used Nmap against them because of its name and Working methodology as It does not complete the TCP handshake, and IDS, IPS cannot detect it.
And Nmap themselves say that it’s stealthy you can read it Here.
Here are some helpful Nmap tutorials:
But we are Wrong!
After Reading this Article You will also be able to Identify Nmap stealth scans by using Wireshark.
I am going to give the results of the analysis I have done between stealth scan -sS (SYN Packet) and TCP connect scan -sT (SYN Packet) and also reasons why stealth scans behave like this!
Why do I analyze against TCP connect scan?
I could analyze the stealth scan against the actual TCP packet, but I have analyzed it against the TCP connect scan. Why? I will give you the answer at the end of the article, so sit back and read!
1. The OPTIONS Field
The OPTIONS Field is only used in the SYN packet when a client initiates a request and when the server replies with SYN, ACK packet, In Both cases the OPTIONS Field is used.
I will not go into the depth of its options but the point to analyze is that:
TCP CONNECT SCAN
In the TCP CONNECT SCAN packet, there are many options given which can be seen in the below image:
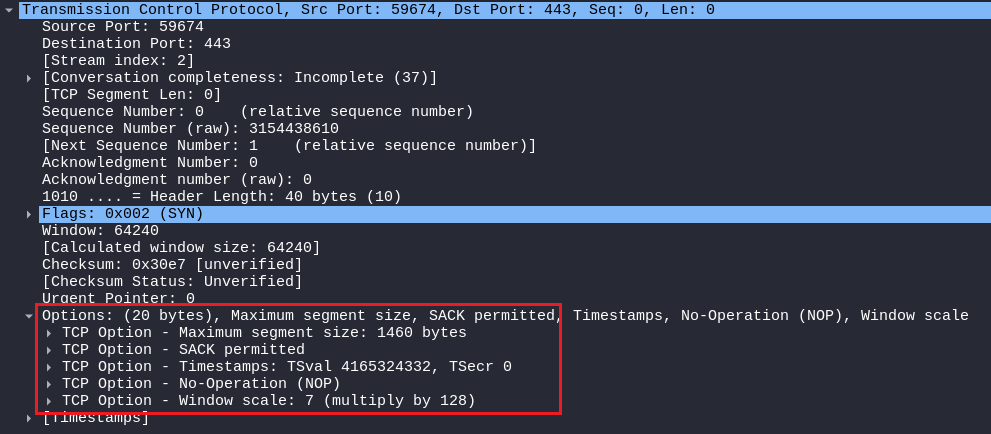
Options are necessary for the client and the server to establish and maintain a smooth connection, it can be seen also that the OPTIONS field consists of 20 bytes.
STEALTH SCAN
But in a Stealth scan packet, there is only one option in the OPTIONS Field which is very rare in real-world scenarios.
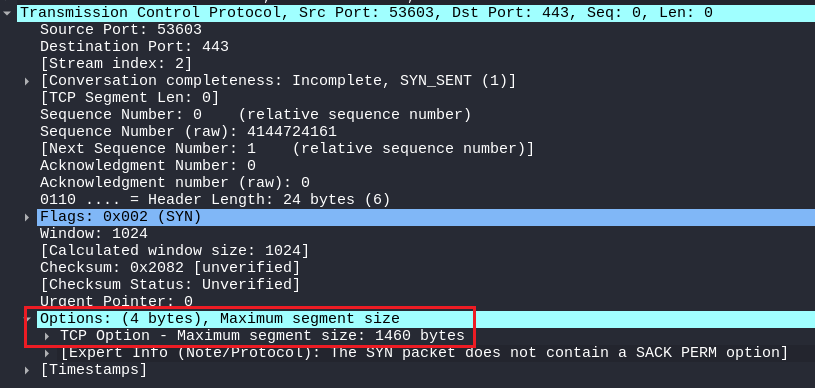
This indication can easily be identified among the real TCP packet and a stealth scan packet used by Nmap!
2. The Window size
The Window size (in Bytes) indicates that if the client is saying to the server that my window size is 64240 Bytes it means that you cannot send me more than that before I acknowledge it! It means that the server has to wait for the ACK packet to be received before sending more data!
Windows size is Directly related to the buffer size.
NOTE: If the client is saying my Window size is 64240 Bytes it doesn’t mean that the server will send 64240 Bytes all at once, It is the buffer size the client can hold at once!
TCP CONNECT SCAN
In the TCP CONNECT SCAN packet, It can be seen that the window size is 64240, Which is normal it can be also around 17,000 or higher as 65,535, Client and server can negotiate and change the window size after the Three-way handshake!
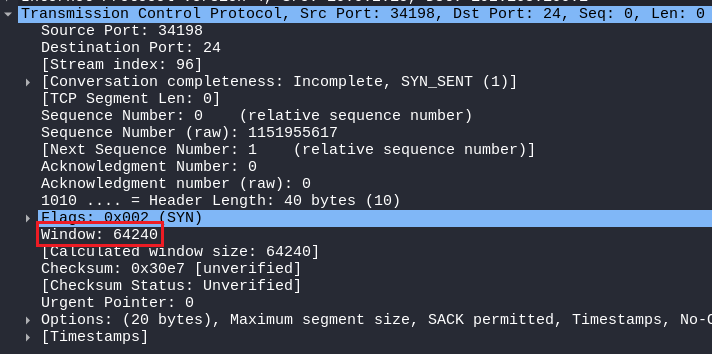
STEALTH SCAN
But in the Stealth scan packet, the window size is too low around 1024 bytes, which is very rare to find in real-world scenarios!
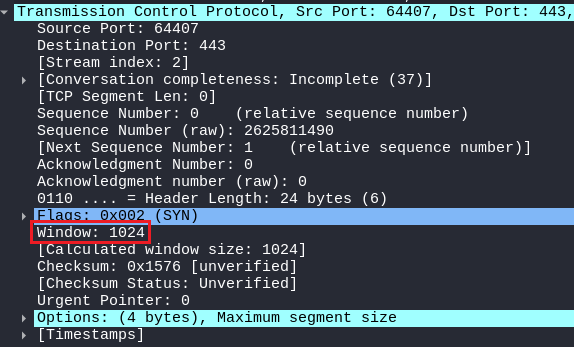
Again, This indication can easily be identified among the real TCP packet and a stealth scan packet used by Nmap!
3. The Header Length
The HEADER LENGTH is the field in the TCP packet that tells the total size of the TCP Header (in Bytes), It does not include the payload but only tells about the size of the TCP Header.
NOTE: The Header Length is Directly related to the OPTIONS Field as discussed above, Because if there are options in the OPTION Field then the size of the Header Length will automatically increase!
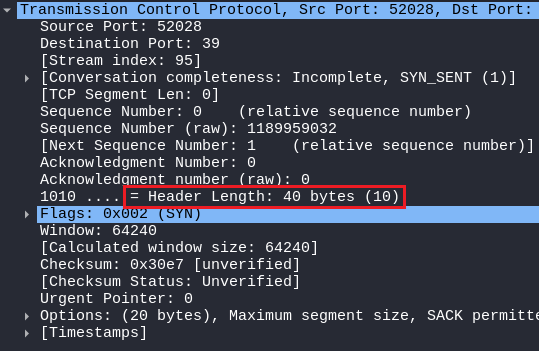
TCP CONNECT SCAN
In the TCP CONNECT SCAN Packet, the HEADER LENGTH is 40 Bytes, as shown in the figure below, It can vary in size, from 20 Bytes (minimum) to 60 Bytes (maximum).
STEALTH SCAN
In the STEALTH SCAN Packet, the HEADER LENGTH is 24 Bytes,
NOTE: As discussed above HEADER LENGTH FIELD is Directly related to the OPTIONS FIELD because OPTIONS FIELD is the only field in the TCP Header that can vary in size the remaining Fields are fixed in size!
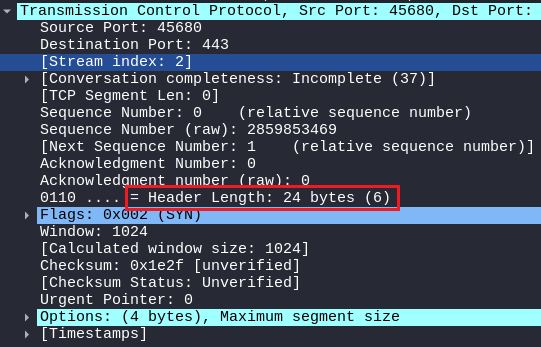
So, indirectly if there are no options or one option in the OPTIONS FIELD then the size of the Header length will vary, which is the indication that with a low Header length of 24 bytes like above there will be only one option, and if the Header length is 20 Bytes then there are no Options.
Again, This indication can easily be identified among the real TCP packet and a stealth scan packet used by Nmap!
4. Sequence Number (RAW)
Sequence Number has an important role in TCP Three-way handshake, It is also known as Initial Sequence Number (ISN). It is randomly generated and used to synchronize client and server, it ranges from 8-10 digits!
When a Client initiates a connection (SYN Packet) a randomly generated sequence number is sent and the server sends an acknowledgment packet by incrementing the sequence number of the client by one.
TCP CONNECT SCAN
To distinguish between a stealth scan and a TCP connect scan by analyzing the sequence number we need more than one (SYN) packet, To accomplish this I used Nmap and scanned multiple ports to get more than one SYN packet.
Here are the results by using TCP CONNECT SCAN:
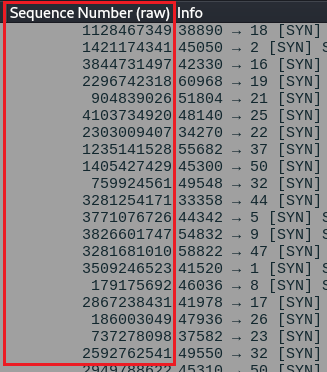
Don’t be confused I Just applied the sequence number filter to get a view of the sequence number of all SYN packets at once!
The thing to note is that TCP CONNECT SCAN tries to mimic real or behaves like a real TCP packet and generates random sequence numbers for each SYN packet. Which is a very great thing in TCP CONNECT SCAN.
NOTE: If we use the timing template -T (with 0 the slowest) with TCP CONNECT SCAN -sT, It will be more difficult to identify that it was scanned by Nmap!
STEALTH SCAN
The dumb stealth scan does not do this, it will not randomly generate the sequence number instead it will use the same sequence number for most of the packet! I mean what the hell!
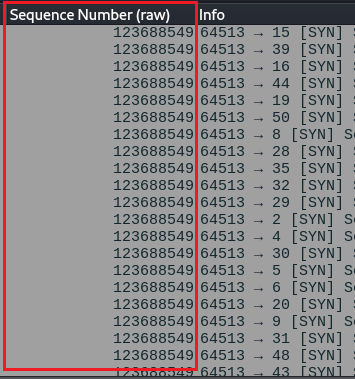
I think this is the most dumb thing that stealth scans do and the easiest thing to identify that it was a stealth scan!
NOTE: You can learn more about TCP Three-way Handshake.
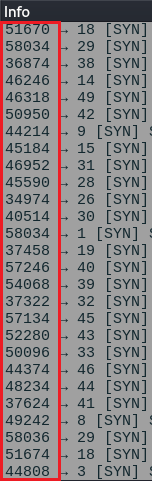
5. Port Numbers
Port numbers identify specific processes running in a computer, port numbers are also randomly generated, it is not possible to find the same port numbers used for the different services in a computer at the same time!
For example, If a client is using port number 45735 for HTTP service at port 80 it cannot use the same port number 45735 for HTTPS service at port 443 at the same time, it has to generate a random port to distinguish from different services running on the same computer.
TCP CONNECT SCAN
The same method is used as we did above in Sequence number, In the TCP CONNECT SCAN different port numbers are used in the SYN packet.
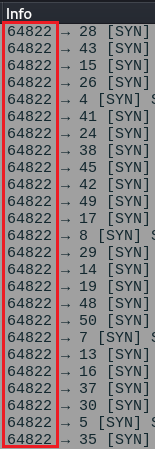
STEALTH SCAN
The dumb stealth scan does the same thing it did in the sequence number, the same port numbers are used!
But why?
There are two questions I promised I would answer them:
The answer is the same:
In the real world, TCP packets are sent by the Transport Layer within the TCP/IP model and it is also responsible for managing it.
When we use Nmap stealth scan the packets sent in stealth scan are sent by the Nmap itself that’s why there is a difference, But when we use the TCP CONNECT SCAN in Nmap what it does that the Nmap does not send it by itself but instead it request the Kernel of the OS Networking stack to send the packet and establish a connection!
That’s why TCP CONNECT SCAN seems real, I mean it is real!
By the way, Today’s security devices like IDS, IPS, and Firewalls can log whether the TCP connection is completed or not just like in a Stealth scan.
