The Ultimate NMAP Tutorial for Beginners in 2025

Last updated: July 07, 2025
Nmap: The Network Mapper, used for Discovering live hosts, Scanning open ports, and Identifying Vulnerabilities.
If you have some knowledge of Computer Networks and the TCP/IP model, then this NMAP Tutorial is for you! I will also give some tips, so sit back and read!
Read Advance Nmap Scanning techniques in 2025
Prerequisite:
There are some Prerequisite, You should know:
ARP Protocol:
Address Resolution Protocol Resolves IP address to MAC address.
ICMP Protocol:
Internet Control Message Protocol is used for Ping request/response. (Type 8 is used for echo messages, Type 0 is used for reply messages)
TCP Protocol:
Transmission Control Protocol is used for reliable communication and performs a Three-way Handshake before sending the data.

- Host (192.168.100.80) requests synchronization with (SYN) Flag. This means that he wants to establish a connection.
- Server (35.190.72.216) reply with (SYN, ACK) Flag. This means Yes of course you can establish a connection.
- Host (192.168.100.80) Acknowledges with (ACK) Flag. This means that a connection is established.
UDP:
User Datagram Protocol is used for fast communication where reliability does not matter. It is the opposite of TCP. It sends the data directly without establishing any connection.
Port Numbers:
Ports are virtual gates or doors where two devices communicate. There are a total of 65,535 Ports in a device.
- 1-1023 is used for well-known services. For example, port 80 for HTTP, port 443 for HTTPS, port 22 for SSH, and so on.
- 1024-49,151 are registered ports for different services.
- 49,152-65,532 are private ports used randomly by clients.
Open Port
While using Nmap you will encounter an Open port which simply means that the service running on that port is listening and it is ready to accept packets.
Closed Port
It simply means that the service on that port is not listening and it will not accept packets if it is sent to it.
Filtered Port
It means that there is a Firewall or any security device that is Dropping the packet and Nmap is not able to identify whether the port is open or closed.
Unfiltered Port
This state means that the port is accessible, but Nmap is unable to identify whether the port is open or closed.
Open-Filtered Port
In this state, Nmap is unable to identify whether the port is open or it is filtered. Because the port does not respond.
Closed-Filtered Port
In this state, Nmap is unable to identify whether the port is closed or Filtered.
Discover Live Host
The First step is to Discover a Live Host in your Network, Before doing port scanning we have to first identify which hosts are live on that network. There are many commands for this:
So first open your terminal in Kali Linux or any distro.
First is the Ping (-sn) command:
It simply Pings the Host by sending an ICMP (type 8) packet and waits for the reply.
nmap -sn <ip-address>In the IP-address option, you can enter one specific IP address or you can enter the whole subnet mask, For example:
nmap -sn 192.168.100.1-255Remember to use the nmap command before each line.
Note: Some scans require root privileges, So make sure you are root!
The result will be:
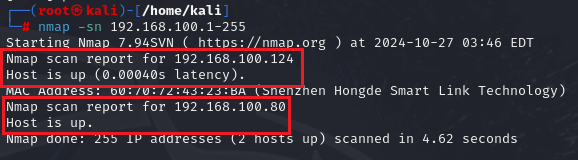
In my case, only two hosts are active in my network.
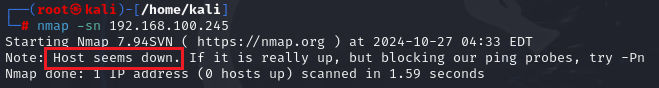
NOTE: Some devices will block ICMP packets which is why it will show that the Host is down, Or the Firewall blocks it, For example:
Other Commands
In the above example, I scanned an IP but it shows it is down, So for this, you can use various commands like:
- -PR (uses ARP protocol to resolve IP address into MAC address)
- -Pn (uses DNS request to identify Host is up or not)
- -PS (uses TCP SYN Flag)
- -PA (uses TCP ACK Flag)
- -PU (uses UDP Protocol)
Remember to use -sn with all of them it means that only do a ping scan and tell whether the host is active or not without doing port scanning, For example:
nmap -sn -PR 192.168.100.245
nmap -sn -Pn 192.168.100.245
nmap -sn -PS 192.168.100.245
nmap -sn -PA 192.168.100.245
nmap -sn -PU 192.168.100.245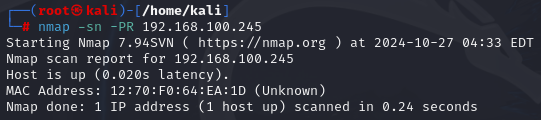
As you can see it worked, So you can try another command as well one by one.
Port Scanning
Till now, You have identified which hosts are up now it is time to scan the ports of that target host, First, we will assume that no firewall will block our scan, and then in the next part we will assume that there is a firewall which is blocking and we have to use invasion techniques but that’s for another part first we will scan the ports:
For scanning Ports there are a lot of different commands which are listed as:
Stealth Scan
- -sS (uses TCP Protocol with SYN)
We have to specify the Port number also, If we don’t specify the port number nmap will scan the ports in random order, For example
nmap -sS -p 1-1500 <ip-address>
OR
nmap -sS -p 22,80,443,1023 <ip-address>So, When specifying the port number by -p commands you can give it a range or you can specify the port number.
NOTE: Nmap stealth scan is not stealthy anymore Here is Why.
How Stealth Scan Works
- The host machine (192.168.100.80) sends TCP packets with the SYN flag set at a specified port number.
- If that port is closed the target (192.168.100.130) will reply with an RST flag.

- If the port is Open the target machine (192.168.100.130) will reply with SYN, ACK flag.
- But, due to the Stealth scan, the Host machine will not reply with the ACK flag instead it will refuse to establish a connection and reply with the RST flag.
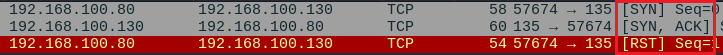
A Stealth scan is non-intrusive as it does not complete the Handshake. This technique helps us to identify Open ports, Don’t worry Nmap will tell us that the port is open the result will be like this:
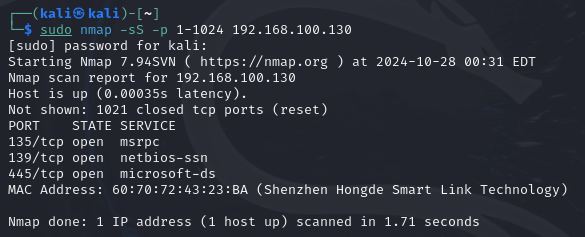
TIP: If you want to scan all the 65,535 Ports at a time, You can use -p- command instead of using -p <port-number>
TCP Scan
- -sT (same as Stealth scan but will complete the Handshake)
It uses TCP Packets with a SYN flag set and completes the Handshake, For example:
nmap -sT -p 1-65535 <ip-address>UDP Scan
- -sU (uses UDP Protocol)
This type of Scan can be used to Bypass the Firewall as UDP Protocol does not need to establish a connection or it does not depend on that there should be a connection established first. For example:
nmap -sU -p 1-2032 <ip-address>TIP: UDP scan (-sU) can be used to bypass static firewalls, If some ports are showing filtered then try -sU if the firewall is static then it will bypass it!
Conclusion
Nmap is a powerful tool for network discovery, port scanning, and identifying potential vulnerabilities. By understanding the basics of network protocols (ARP, ICMP, TCP, UDP) and port states (open, closed, filtered, etc.), you can efficiently use Nmap to gather information about live hosts and open ports in a network.
This was all about the Basic Nmap commands. I hope you understand and it will help you.
