Assessment Methodologies: Information Gathering CTF 1 — eJPTv2 Walkthrough
Last updated: July 09, 2025
Hi everyone! In this article, we will solve the Assessment Methodologies: Information Gathering CTF 1 (eJPTv2). I will not share the flags because I don’t want you to copy and paste them, but rather solve it yourself and follow my instructions, so sit back and read!
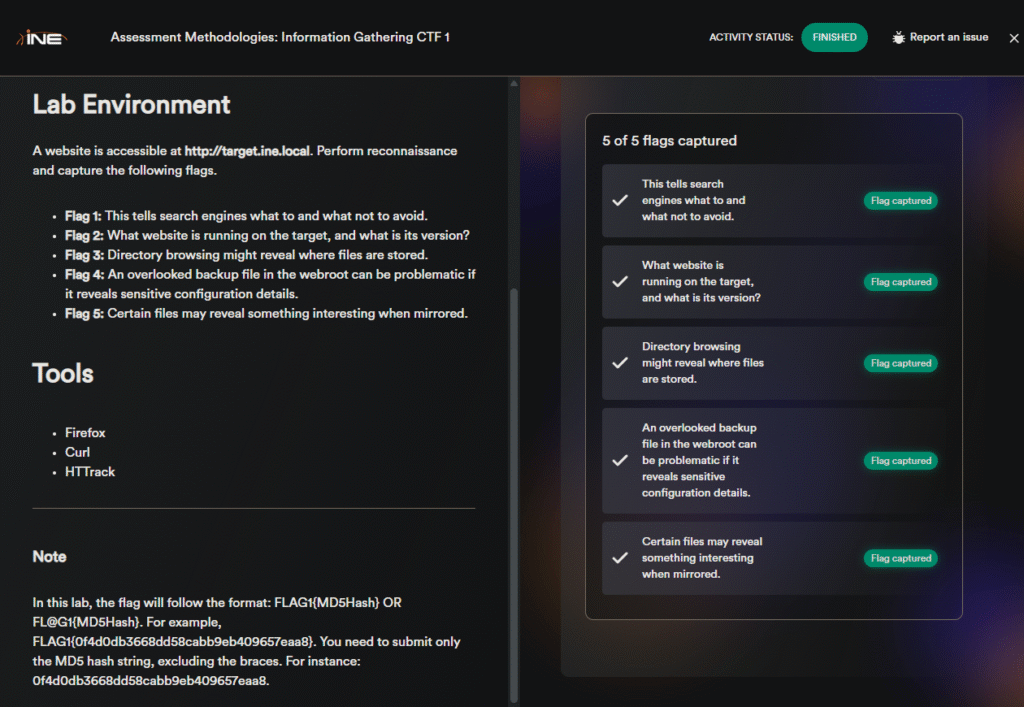
Flag 1: This tells search engines what to and what not to avoid.
It’s the robots.txt file that tells the search engines what to crawl and what not to, so head towards the browser and view the robots.txt
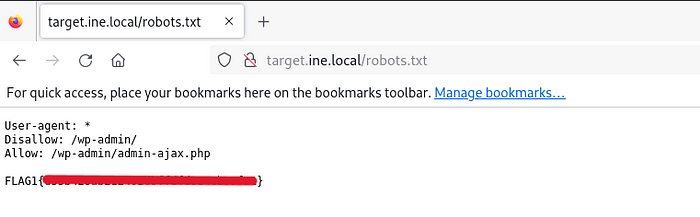
Flag 2: What website is running on the target, and what is its version?
We have to do a simple nmap scan to identify which website is running and its version on the target system. For this, we will utilize the Default scan of nmap, We have to use the -sC option to get more information
nmap -sS -sV -sC target.ine.local
Flag 3: Directory browsing might reveal where files are stored.
hmm… Directory browsing, I think we have to brute-force the directories using gobustor or dirb, let’s do it quickly
dirb http://target.ine.local
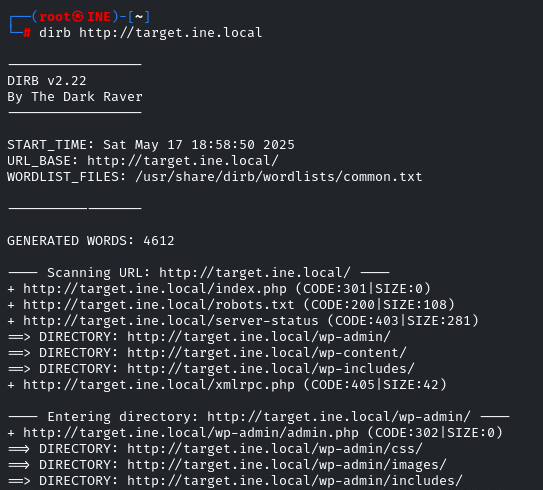
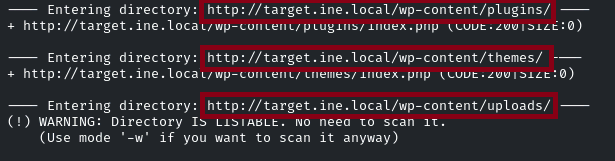
So we have identified some directories. We have to explore it one by one and look at it manually
After exploring one by one, the directory /wp-content/uploads has an interesting file:
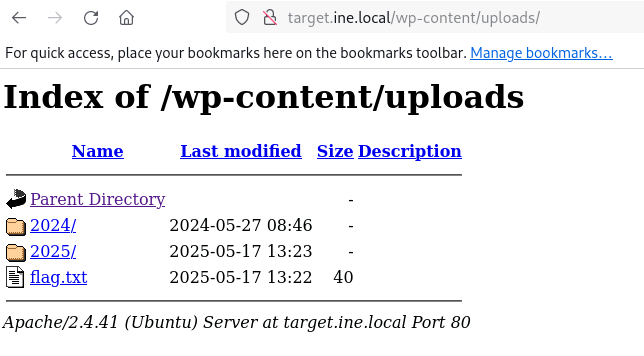
Flag 4: An overlooked backup file in the webroot can be problematic if it reveals sensitive configuration details.
As we know, the website is running on WordPress, which was initially identified. Now we have to look into the backup files of WordPress
so the backup files in WordPress are stored in /wp-config.bak path
Just navigate into it, and it will start downloading
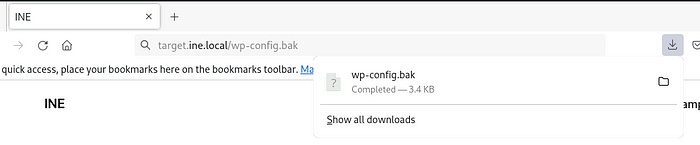
It will be downloaded automatically as soon as you navigate into it,
then view the file,
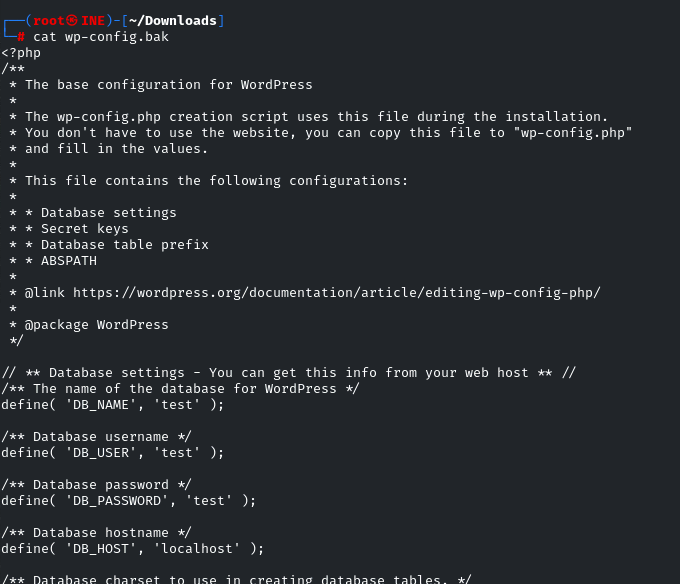
scroll down a little bit
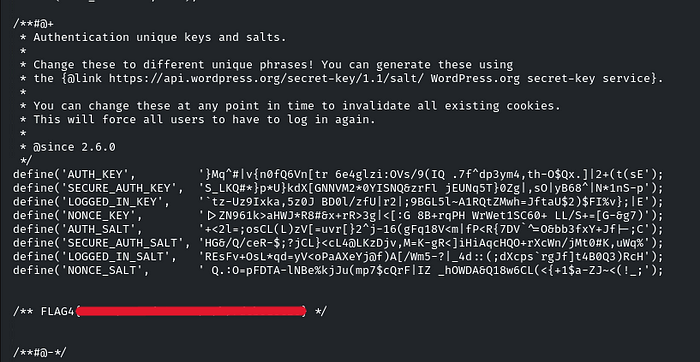
and there will be the flag
Flag 5: Certain files may reveal something interesting when mirrored.
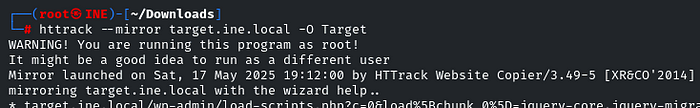
Mirrored…Are you thinking what I am thinking? Guess it! HTTrack! yes do it
httrack --mirror target.ine.local -O Target
It will store all the output into the Directory named “Target”, so we can easily find the flag by using the grep utility, because there are a lot of files we cannot find the flag manually
Now, grep it. We know that all the flag formats were like FLAG1, FLAG2, FLAG, and a number. As it is the fifth flag, it will be “FLAG5”, just grep it! It will find the flag in the directory Target, which we mirrored and saved the website
grep -i "FLAG5" -R Target
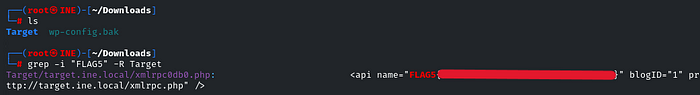
And there you go! It was pretty easy. See you in the next Challenge!
Good luck hackers
