Assessment Methodologies: Vulnerability Assessment CTF 1 — Walkthrough
Last updated: July 12, 2025
Hi everyone! In this article, we will solve the Assessment Methodologies: Vulnerability Assessment CTF 1 (eJPTv2). I will not share the flags because I don’t want you to copy and paste them, but rather solve it yourself and follow my instructions, so sit back and read!
Flag 1: Explore hidden directories for version control artifacts that might reveal valuable information.
The question gives us a hint that we have to find directories on the website for version control. Git is a famous version control system. So, first of all, do a nmap scan:
nmap -sS -sV target.ine.local
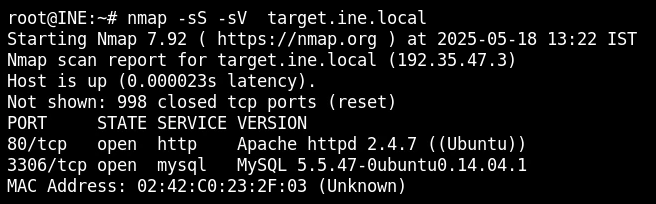
So, a web server is running on port 80, but we need to enumerate the directories on the web to find the version control directory. So we will do the default script scan on port 80
nmap -sS -sV -p 80 -sC target.ine.local
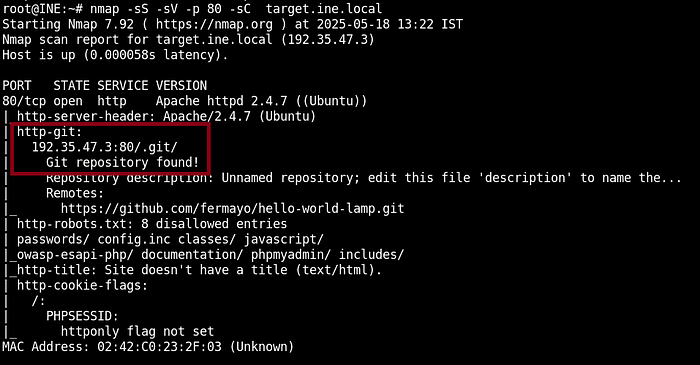
So we have found the “/.git” directory. Fire up the web browser and head towards it
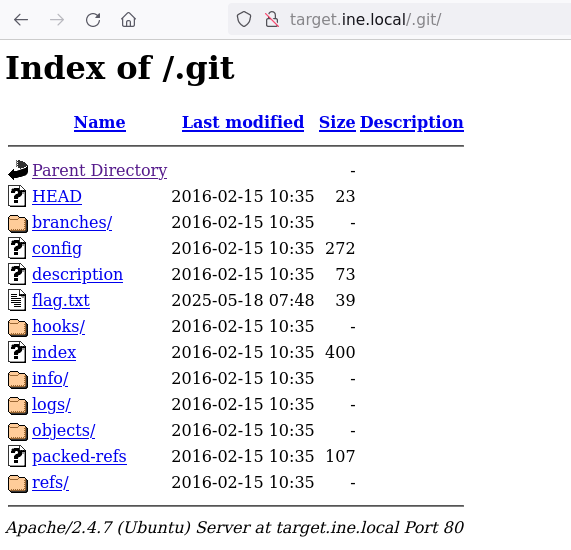
There is the flag!
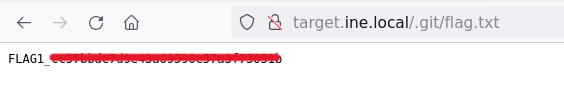
Flag 2: The data storage has some loose security measures. Can you find the flag hidden within it?
Now we have to enumerate more on the web server. For this, we will use the “http-enum” script in nmap
nmap -sS -sV -p 80 --script=http-enum target.ine.local
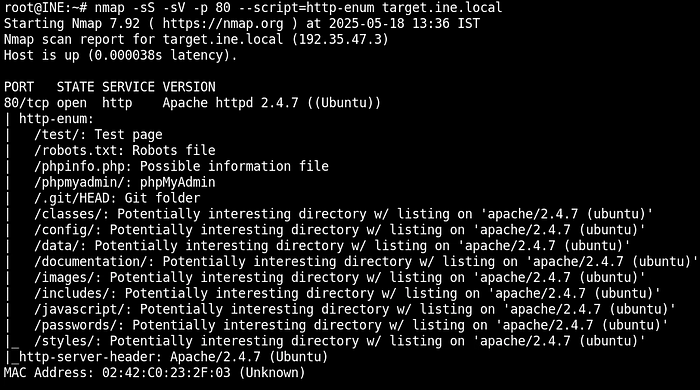
So by running the script “http-enum” we have got some interesting files, robots.txt, phpinfo.php, phpmyadmin, and .git. We have already explored .git, so let’s go to the /phpmyadmin as it is the main hub to manage the Database, and there might be the flag.
Navigate to the /phpmyadmin
As in the question, “The data storage has some loose security measures”. The data storage usually means MySQL because data is stored in an SQL database, so on the left side there is the “mysql” section, so navigate into it
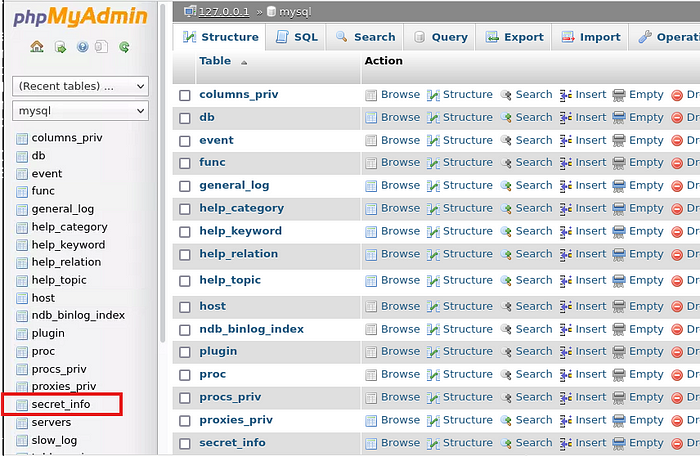
hmm… “Secret_info” is interesting, navigate into it
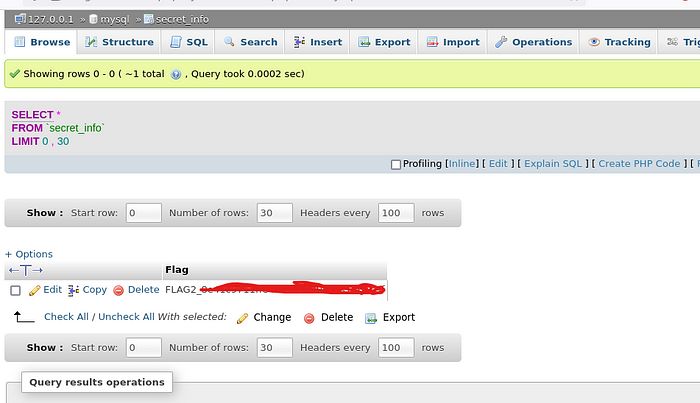
There is the flag!
Flag 3: A PHP file that displays server information might be worth examining. What could be hidden in plain sight?
Remember the nmap scan, there was a /phpinfo.php file, let’s navigate into it
Scroll down a little bit.
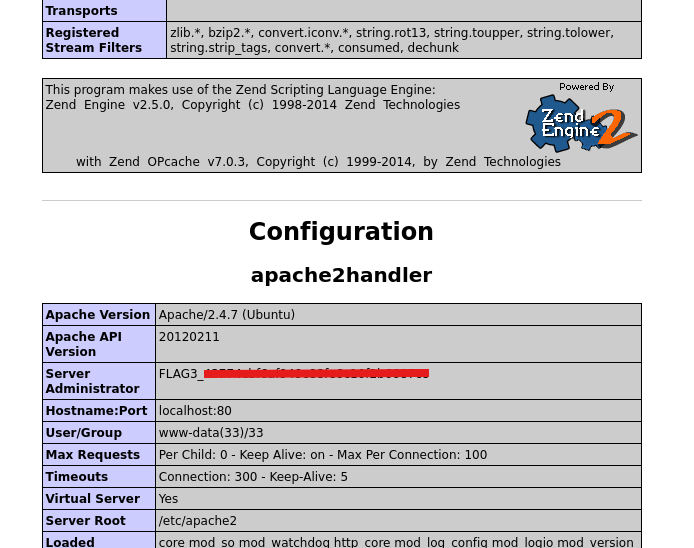
Flag 4: Sensitive directories might hold critical informationSearchh carefully for hidden gems.
We explored the “/.git”, “/phpinfo.php”, and “/phpmyadmin”, now the “/robots.txt” remains
/robots.txt file should not be overlooked as sometimes it contains valuable information!
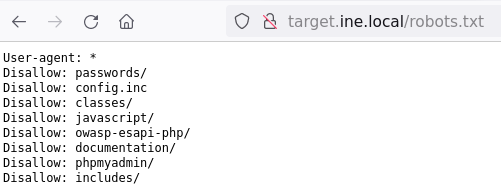
The “passwords” directory looks interesting. Navigate into it
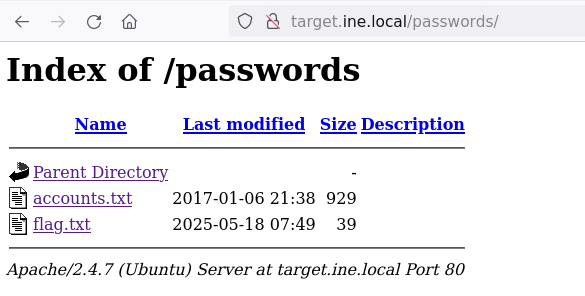
Yes! There is the flag
And there you go! It was pretty easy. See you in the next Challenge!
Good luck hackers
