How Does Ransomware Attack Work

Last updated: July 07, 2025
I will explain how ransomware attacks work in detail, from creating the ransomware to encrypting and decrypting files. I will be also telling about the case study on the famous wannacry ransomware attack, like how it worked, which vulnerability was exploited, How it became persistent, and much more. You can also have a look at the topics I will go through below. So sit back and read!
Terms You Should Know
Before Diving into the topic, I hope that you know some terms related to this, if not I am here to help you, Below are some terms you should know:
Ransomware
Ransomware is a type of malware that encrypts the data in the victim’s machine which becomes unusable and demands a ransom (money) in the form of Bitcoins, If the payment is given then the attacker decrypts the file.
Symmetric Encryption:
Symmetric means the Same, So in this type of Encryption, the same key is used for encrypting and decrypting.
Asymmetric Encryption:
Asymmetric means Different, So in this type of Encryption, Different keys are used for encrypting and decrypting. Public key – For encrypting. Private key – For decrypting.
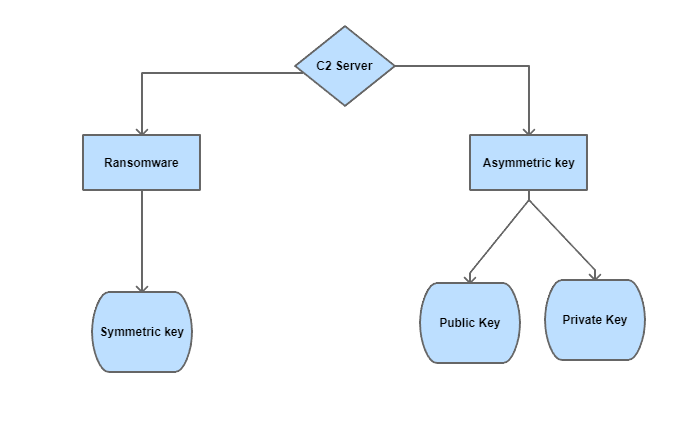
Step 1: Setting Up the C2 Server
Setting Up the C2 server and creating the ransomware is the main task for a successful ransomware attack, It can be separated into two parts: First: The attacker sets the Command and Control server, which can generate its Asymmetric Keys (public and private key) Second: The attacker programs the ransomware in C/C++ language, the ransomware can also generate its Symmetric key, search for valuable files, remain persistent, etc.
Step 2: Sending Ransomware
For institutional victims, the ransomware needs to be specifically targeted and highly sophisticated. This is because, usually, some form of security defense is already in place. Some common infection vectors are email attachments, email links, compromised websites, and social media. The sending of ransomware malware to the target depends on how effective social engineering is exploited.
Step 3: How Ransomware is Persistent and Stealthy
When the payload has reached the victim’s system, the ransomware setup behavior may begin, But before doing encryption, there are some tasks the ransomware should perform which are given below:
Payload persistence
What if after encrypting all files in the target system and displaying the ransomware note to the victim, but the victim simply reboots the infected computer and the ransomware has gone? Hackers are not dumps.
So before doing encryption, the Attacker ensures that the attack should be persistent even after the system is rebooted.
but How?
- Placing the executable file in the system startup directory, The startup directory is a folder in an OS like Windows that contains programs set to run automatically when the computer starts, so the attacker places a malicious executable file (which is part of ransomware) in system startup directory so whenever the system reboots the ransomware launched automatically. C:\Users[Username]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
- Adding a new registry key: The Windows registry is a database used by the OS to store system settings and configurations, and instructions for programs to run during startup, So attackers add or modify certain registry keys to ensure that their ransomware is loaded every time the system starts.
- Or Setting a scheduled task: The attacker creates a scheduled task that instructs the OS to run the malicious program (ransomware) at a specific time or event, for example, a scheduled task can be set to run that ransomware program at a specific event like when the system is rebooted.
Restricting system restore
The next step is to restrict the victim from restoring the system,
- The attackers might delete the scheduled backups,
- Also, delete restoring points of the system like snapshots at specific times.
Stealth mode
There are some techniques that attackers will use (100 % guaranteed) if the attacker is a pro. Whatever the attacker wants to execute in the victim’s device will be executed from the %AppData% directory using the names of common system executable programs.
- %AppData% is a directory that is a hidden folder in Windows where applications store user-specific data and settings, It is commonly used by legitimate software to store files, So some antivirus programs may not closely monitor this folder. Ransomware placed in the %AppData% directory often gets executed automatically when the system starts so also ensuring persistent as I discussed above about persistent.
- The attacker will use common names of legitimate files like explorer.exe, svchost.exe making it harder to get noticed by victims or antivirus software
WannaCry Persistent Mechanism:
- The persistent mechanism in wannaCry ransomware was that the malware attempts to create a mssecsvs2.0 process with the Display Name of “Microsoft Security Center (2.0) Service”.
- WannaCry creates an entry in the Windows registry to ensure that it runs every time the computer is restarted
- Attempts to achieve memory persistence by adding itself to the AutoRun feature of Windows.
- Uses the Windows icacls command to grant itself full access to all files on the machine.
- Deletes all backup (shadow) copies and tries to prevent being booted in safe mode by executing several commands in the Windows command line
- Deletes all backup folders
- Tries to kill SQL and MS Exchange database processes by executing several commands in the Windows command line
Environment mapping
It is a technique used by malware (specifically ransomware ) to determine whether it is running on a real machine or it is a honeypot or sandbox environment, After encrypting the files and displaying the note on the machine the attacker comes to know that it was a honeypot!
- The ransomware will check the system security settings to see if it is on a real machine because on a real machine antivirus, firewalls, and other security mechanisms like HIDS, and HIPS are typically enabled.
- The ransomware will check the geographical location based on the IP address, timezone, or language settings to verify it is the real machine in a specific region.
- The ransomware will check the file system architecture, like Disk size because the virtual environment has fixed and small disk partition, and file structure, it can check the presence of certain system files missing or altered files or directories, which can indicate it is a sandbox environment.
- The ransomware also checks the presence of network drives or connected devices.
Privilege Elevation
The attacker should elevate to the administrator level to ensure that the ransomware will perform all the actions without restrictions like deleting backups, executing commands from %AppData%, adding registry keys, and disabling security programs as discussed above.
How it is done?
Privilege elevation is typically done by exploiting vulnerabilities already present in the system, bugs, or flaws.
WannaCry Used Exploits:
WannaCry uses the EternalBlue and DoublePulsar exploits that were allegedly leaked in April 2017 by a group called The Shadow Brokers. EternalBlue exploits the server message block (SMB) vulnerability that was patched by Microsoft on March 14, 2017 (MS17-010), this vulnerability allows to execute a remote code on the infected machines by sending specially crafted messages to an SMB v1 server, connecting to TCP ports 139 and 445 of unpatched Windows systems. In particular, this vulnerability affects all unpatched Windows versions starting from Windows XP to Windows 8.1, except for Windows 10.
DoublePulsar is a persistent backdoor that may be used to access and execute code on previously compromised systems, thus allowing the attackers to install additional malware on the system. During the distribution process, WannaCry’s worm component uses EternalBlue for initial infection through the SMB vulnerability, by actively probing appropriate TCP ports and, if successful, tries to implant the DoublePulsar backdoor on the infected systems.
Once the setup is complete, the ransomware may contact the Command and Control Server for several reasons, the most common being to obtain the encryption key for the encryption process. Another possible reason is to download more files for a more advanced infection search.
Step 4: Encryption process
After obtaining the encryption key, the ransomware can start searching for seemingly valuable files such as text documents, spreadsheets, presentations, images, and databases, Encrypting files involves further steps:
- Ransomware finds a file or database to encrypt it, most of the ransomware also targets the backup systems to prevent recovery.
- After finding the files or database to encrypt, ransomware generates its symmetric key (same key for encryption and decryption) AES 256-bit algorithm, then this key is used to encrypt the targeted files.
- The ransomware receives the public key (RSA algorithm) from the C and C server to encrypt the symmetric key, if there is any symmetric key in plain text it would be deleted.
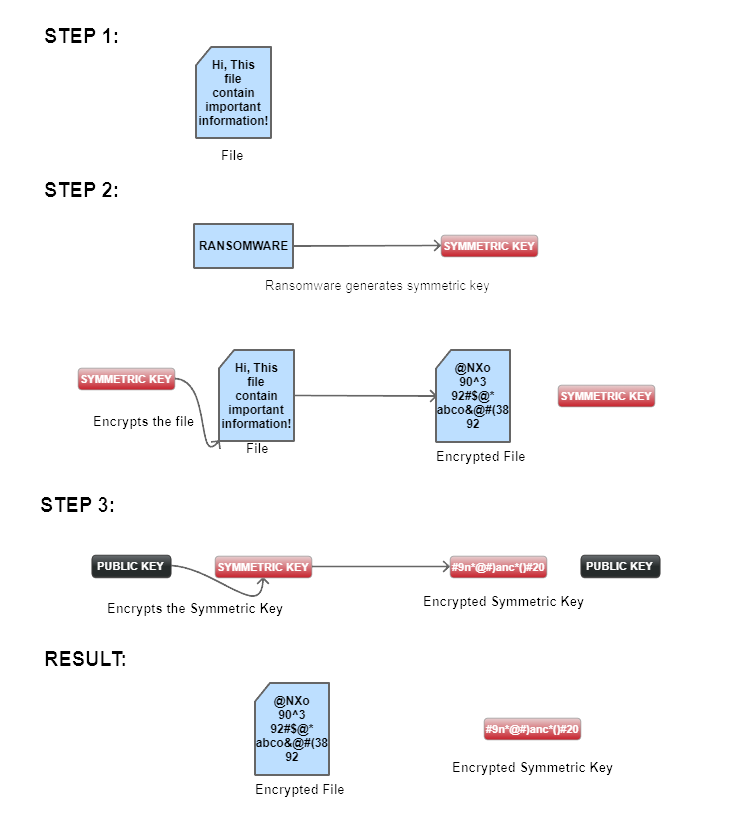
Now to decrypt the files private key is required from the C and C server. Which is under the control of the attacker.
By the way, the Encryption process can be classified into three classes:
Class A: The file is only Encrypted.
Class B: The file is encrypted and renamed.
Class C: The file is encrypted, renamed, and relocated.
WannaCry Encryption:
WannaCry ransomware used the same Encryption process as discussed here.
Step 5: Demanding Ransom
After the above steps have been completed, the next step is to demand the ransom, which is done simply by displaying the ransom demand. The demand note will inform the victim of the infection, and specify the mode of payment and communication, if the payment deadline is acceded the ransomware will start deleting files.
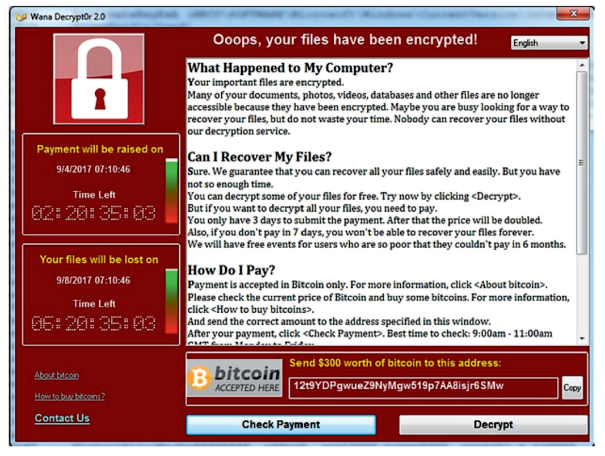
Wannacry demanding Ransom:
As you can see, this was the note displayed when wannacry ransomware attack happened, The noticing thing is that on the left side of the image, it is written that the files will start deleting as time exceeds, So not only Encrypting the files and demanding money for decryption but also extorting to delete the files.
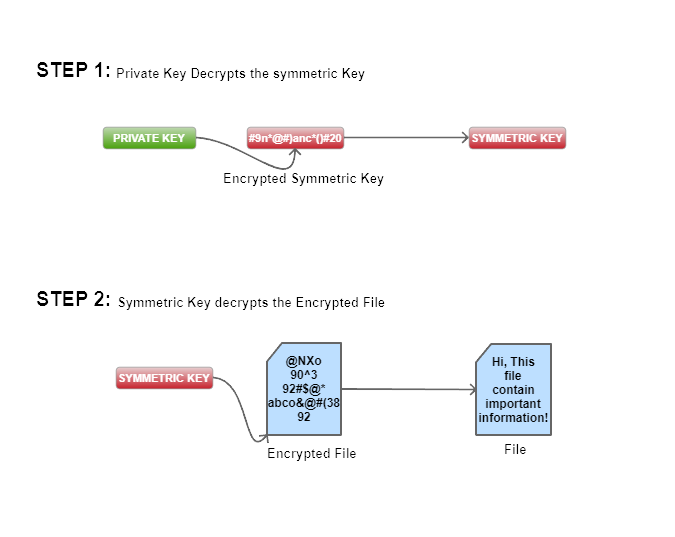
Step 6: Decryption process
After paying the ransom,
- The ransomware gets the private key from the c and c server
- Which decrypts the symmetric key
- That symmetric key is then used to decrypt the files.
Thanks for reading this article, if you have any suggestions or want to give feedback feel free to reach me out!
