How to Bypass a Windows Firewall using Nmap

Last updated: July 07, 2025
Nmap: The Network Mapper, used for Discovering live hosts, Scanning open ports, and Identifying Vulnerabilities.
Let’s jump in and do not waste time!
Nmap
If you are a beginner and do not know how to use Nmap, so don’t worry Here is the Tutorial for it!
Now, Open your Linux Terminal and Identify the Windows machine!
First, we will use:
nmap -sA -p <port-number> <ip-address>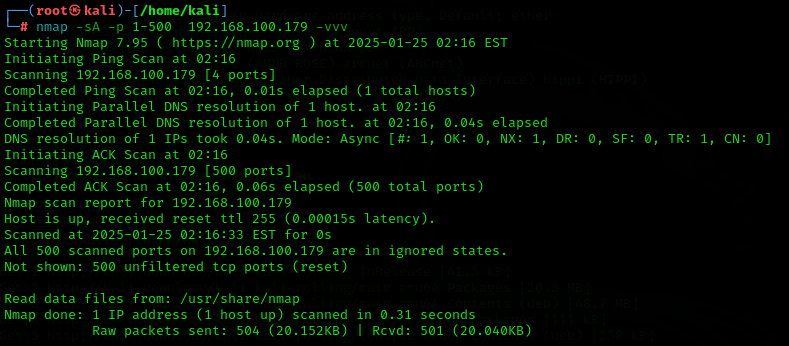
As you can see, all the ports are in the ignored states, now let’s use that command!
Nmap -sT Command
Yes! A TCP connect scan can help us bypass the Windows firewall, but why? Here is the answer
nmap -sT -p <port-number> <ip-address>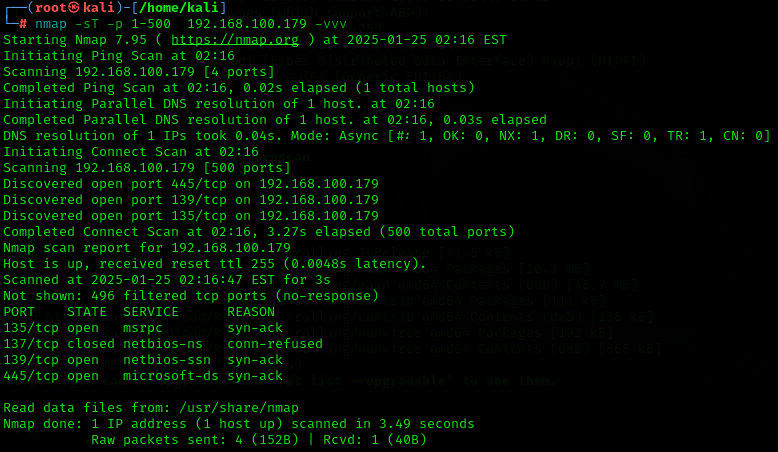
You can see it now! TCP connect scan successfully bypassed the Windows firewall! Is it that simple?
Reason
In the real world, TCP packets are sent by the Transport Layer within the TCP/IP model and it is also responsible for managing it.
When we use Nmap stealth scan (-sS or -sA, etc) the Nmap itself sends the packets sent in stealth scan that’s why there is a difference, But when we use the TCP CONNECT SCAN in Nmap what it does that the Nmap does not send it by itself but instead it request the Kernel of the OS Networking stack to send the packet and establish a connection!
That’s why TCP CONNECT SCAN seems more real than stealth scan (-sS or -sA, etc) and can bypass stateless firewalls!
