Nmap Vulnerability Scan

Last updated: July 07, 2025
Nmap: The Network Mapper is a powerful tool for Vulnerability scanning and scanning ports. In this article, I will explain how to use Nmap for vulnerability scanning. So sit back and read!
Here are some helpful Nmap tutorials:
What is the Nmap Scripting Engine
The Nmap Scripting Engine (NSE) is a very powerful feature within Nmap, It can be used to run different types of scripts used for different purposes, Below are some types of scripts that Nmap supports with their Description:
| Script Category | Description |
|---|---|
| Auth | Authentication related Scripts |
| Broadcast | Discover Host by sending Broadcast message |
| Brute | Brute-force Attack |
| Discovery | Discover Host by sending a Broadcast message |
| dos | Detect targets vulnerable to Dos attack |
| Exploit | Attempts to exploit various vulnerable services |
| Safe | Discover Host by sending a Broadcast message |
| Malware | Scans for Backdoor |
| version | Retrieves Service Version |
| Vuln | Scans for Vulnerability |
TIP: YOU CAN FIND ALL OF THE SCRIPTS IN YOUR KALI LINUX MACHINE IN THIS DIRECTORY: /usr/share/nmap/scripts
Default Scripts
- -sC OR –script=default
Both commands run the scripts on the target machine using the Default set of scripts, Default script may not tell you the CVE vulnerabilities present in it, But may give some sort of Information about it like DNS servers, SSL certs, etc!
nmap -sC -p <port-number> <ip-address>
OR
nmap --script=default -p <port-number> <ip-address>LETS JUMP INTO OUR MAIN GOAL!
Vuln Script
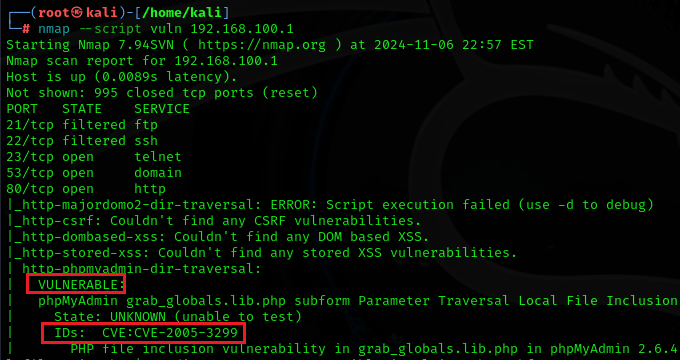
As mentioned above in the table we will be using the Vuln category to scan for CVE Vulnerabilities. There are actually different types of Methods and scripts for vulnerability scanning in Nmap, Vuln is one of them! Vuln script is already present on the Nmap by default, You have to run it only!
TIP: BEFORE RUNNING VULN SCRIPT, RUN nmap –script-updatedb , NMAP WILL UPDATE ITS DATABASE IF NEW SCRIPTS ARE RELEASED!
- –script vuln
This script scans for the CVE vulnerabilities present in the system by using already scripts present in the Nmap, FOR EXAMPLE:
nmap --script vuln -p <port-number> <ip-address>TIP: FIRST SCAN ALL THE PORTS AND IDENTIFY THE OPEN ONES, THEN WHILE RUNNING THE VULN SCAN AS ABOVE, INCLUDE ALL THE OPEN PORTS
Vulners Script
The second method is to use Vulners script, Nmap does not contain this script by default so you have to install it from GitHub:
sudo git clone https://github.com/vulnersCom/nmap-vulners.gitAfter installing it make sure it is in the right directory by:
ls /usr/share/nmap/scripts | grep nmap-vulnersIf the result is nmap-vulners then it is right!, So let’s jump in! The command For this will be:
- –script vulners
nmap -sV --script vulners -p <port-number> <ip-address>If this doesn’t work then try to specify the path to the vulners.nse file, For example:
- –script=nmap-vulners/vulners.nse
As nmap-vulners/vulners.nse directory is in the default nmap’s directory ( /usr/share/nmap/scripts ) then specifying the path may work, For example:
nmap -sV --script=nmap-vulners/vulners.nse -p <port-number> <ip-address>Vulscan Script
The third and last CVE Vulnerability scanning script is Vulscan, Same as Vulners script you have to install it from GitHub, But to install it there are some steps to follow,
First, Go to below mentioned directory:
cd /usr/share/nmap/scriptsSecond, Simply copy the below command and paste and run it:
git clone https://github.com/scipag/vulscan scipag_vulscan
ln -s `pwd`/scipag_vulscan /usr/share/nmap/scripts/vulscanThird, By going to the /usr/share/nmap/scripts/ Directory make sure that there is vulscan directory and by going inside it there will be scipag_vulscan directory (may or may not be present so don’t worry we need vulscan.nse file just remember the path) and then it will contain vulscan.nse file, remember it!
So To run Vulscan script the command will be:
- –script vulscan
nmap --script vulscan -p <port-number> <ip-address>Same as for vulners script but, if this is not working then again do the same thing as we have done for vulners script specify the path:
- –script=vulscan/scipag_vulscan/vulscan.nse
If your path is different to vulscan.nse then you can adjust with that!
nmap --script=vulscan/scipag_vulscan/vulscan.nse -p <port-number> <ip-address>NOTE: TO UPDATE THE DATABASE OF VULSCAN SCRIPT, JUST GO TO /usr/share/nmap/scripts/vulscan/scipag_vulscan directory and first run chmod 744 update.sh and then run ./update.sh
SUMMARY
For vulnerability scanning, there are mainly three types of scripts: vuln, vulners, and vulscan, each with its own advantages and disadvantages. It could be possible that vulners and Vulscan may not work correctly, but Vuln, which is by default in Nmap, will definitely work.
