TCP 3-WAY Handshake analysis with Wireshark

Last updated: July 07, 2025
Wireshark:
Wireshark is a tool for analyzing packets in a network, also known as a Network Protocol Analyzer. It gives you an interface to troubleshoot the network or learn about networks and different protocols, just like us! Wireshark comes pre-installed in all Linux Distributions.
In this article, I will analyze the TCP 3-Way handshake (SYN, SYN/ACK, ACK) using WireShark. If you are curious to learn the TCP 3-way Handshake in Detail then this Article is for you!
I will also go through all the fields found in TCP Header Format and their role in 3-way handshake. So sit back and read!
Sequence Number
We will first focus on Sequence Number or Initial Sequence Number (ISN), It will be essential and can also be called the Backbone of TCP 3-way Handshake. To establish a connection between client and server Sequence Number plays an important role, Here is a picture of a Three-way handshake:

You have seen and heard a lot about SYN, SYN/ACK, and ACK. But what’s going on at the packet level? Let’s dive in!
SYN
SYN means to synchronize the sequence number on the both client and server side, Sequence Number is always randomly generated. But How it is synchronized?
Let’s analyze the Sequence Number (RAW) of the SYN Packet:
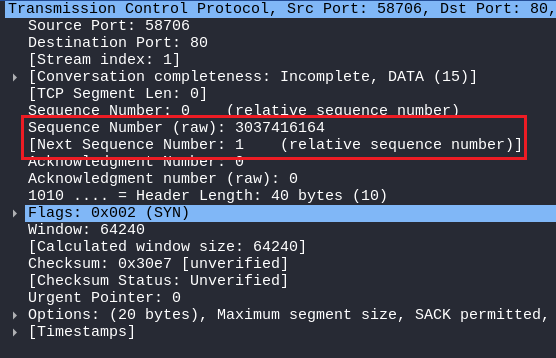
In this SYN packet, it shows 3037416164 as a Sequence Number. Below that, it can also be seen that the Next Sequence Number is 1, which means the client is expecting the server that reply to me with an increment by one in sequence number, although it’s not part of the Header format of TCP, Its the wireshark telling us.
The client is saying to the server “3037416164 is my sequence number, and increment it by one so that I would know you heard my request”
SYN/ACK
Now the server replies with the SYN/ACK, You know why it is called SYN/ACK because the server is acknowledging the sequence number sent previously by the client with incrementing by one and also sending its own SYN so that the client can now acknowledge it!
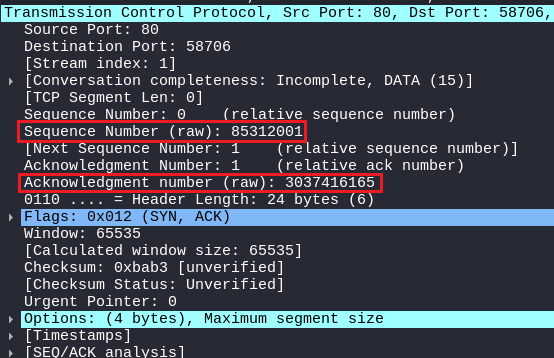
So again it can seen that in SYN/ACK, Firstly the server is sending its sequence number which is again a random number (85312001). secondly, the server acknowledges the previous sequence number sent from the client by incrementing it by one (3037416165)
ACK
The last packet in the TCP 3-way handshake is the ACK, as we know from the previous message server replied with SYN/ACK, the server acknowledged it by incrementing the sequence number by one and we came to know that the server was online and listened to us and also sent it own randomly generated Sequence Number (SYN).
Now it’s time for the client to acknowledge it by incrementing it by one.
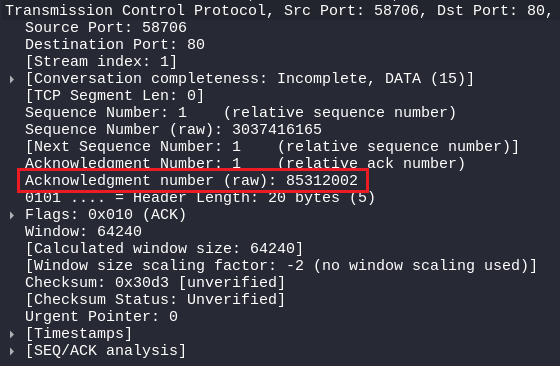
So it can be seen that in the ACK packet, the client acknowledges it by incrementing the previous number by one. (the SYN was: 85312001, ACK: 85312002)
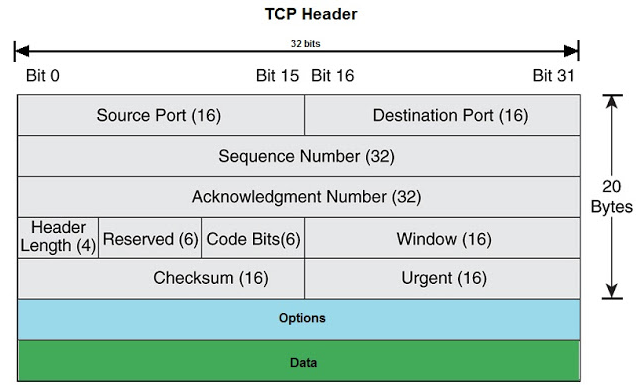
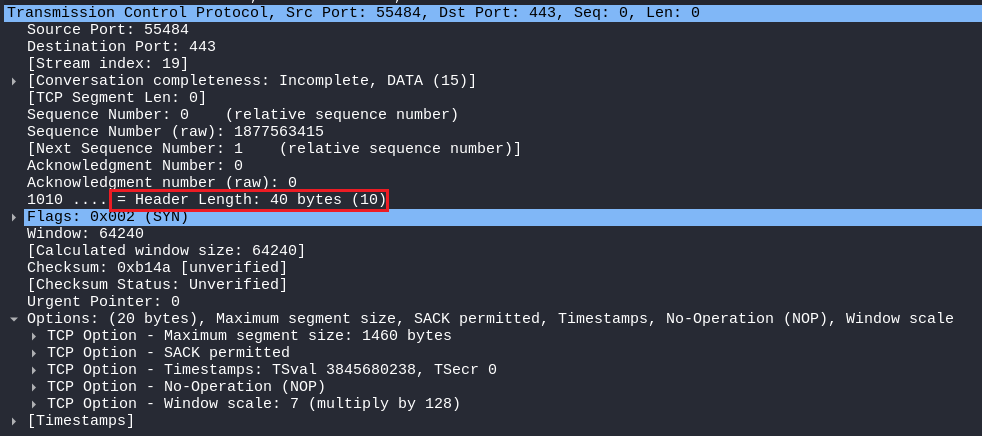
Header Length
As the name suggests, It is the length or size of the TCP Header in Bytes. It only includes the TCP Header not the data in it!
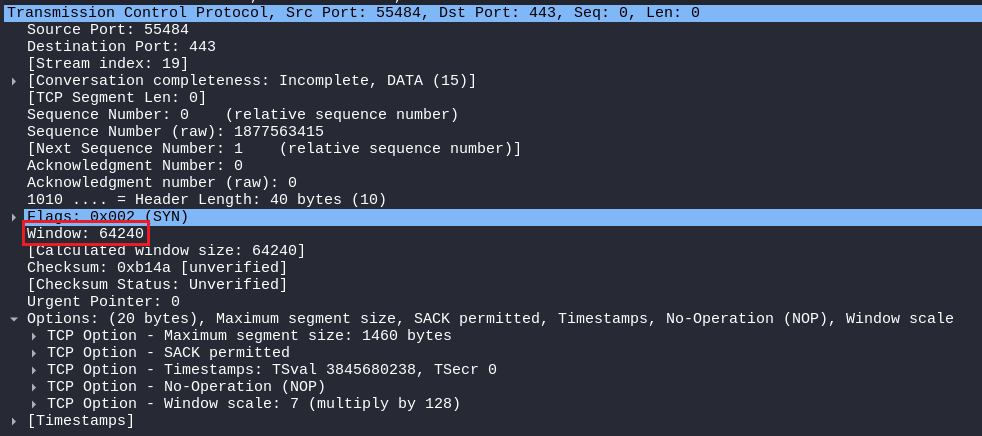
Window
The window size directly indicates the buffer size of the host (whether it is the client or the server), So it means that the client is saying “My maximum buffer size is 64240 bytes if you sent me that amount of data then you have to wait for my ACK before sending more data, So that I can free up my buffer.”
NOTE: The Server Does not send that much amount of data at once it is a theoretical value the actual amount depends upon the MAXIMUM TRANSMISSION UNIT (MTU)
Checksum
Checksum is a mechanism to ensure data integrity when transmitted, it ensures that the data is not been altered in the path, It is calculated by a mechanism that adds some bits from the header, If the calculated checksum on the receiver side does not match the checksum sent by the sender then it means the data has been altered!
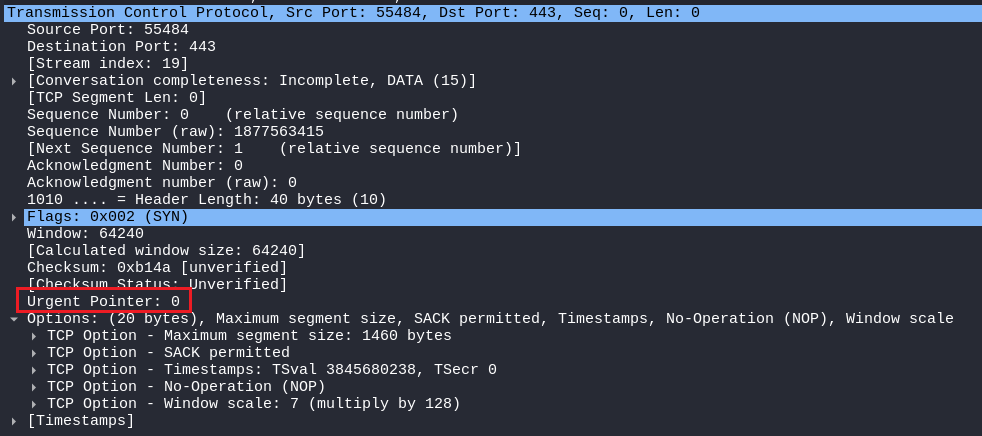
Urgent Pointer
Urgent Pointer is used to indicate that data that is urgent is present in the TCP segment, It may be a last bit in the segment! Urgent Pointer is used with the conjunction of Urgent Flag.
Options
As the name suggests, the Options Field in the TCP provides options that can only be found in the SYN Packet, As the client is initiating the connection it will provide options in the option field and when the server replies with SYN/ACK server will also provide the options for the client.
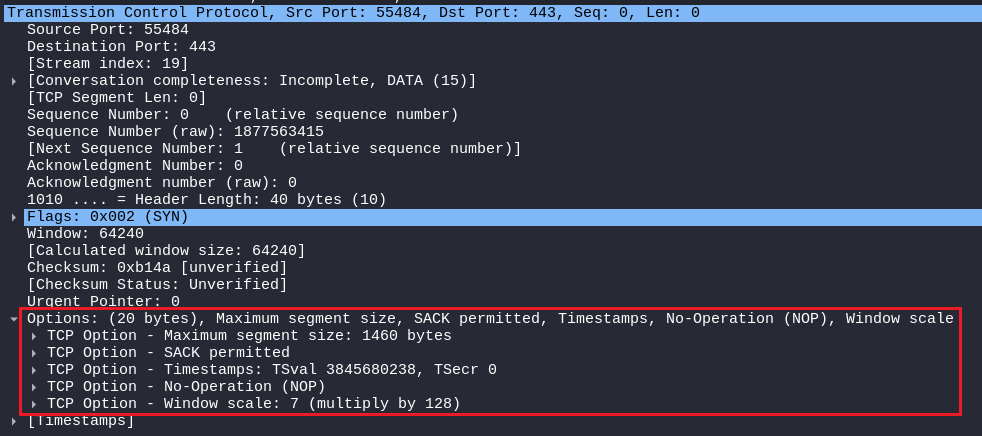
As in this SYN packet, the client is providing different Options for the server let’s have a closer look at each of the options:
Maximum Segment Size (MSS):
MSS shows the maximum size of the payload or data (excluding the header size) the host can handle at one time. In the above example, the client is saying, ” Do not send me data more than 1460 bytes at once.”
NOTE: MSS is an advertisement message, client and host do not negotiate about it!
Window scale:
The window scale gives the option to the client or the server that multiply the window size by a specific number whatever the answer is that will be my buffer size!
Timestamps:
Timestamps give the time taken for the round-trip, For example, if an SYN packet is sent the timestamp will be recorded and when the server replies, the timestamp will be recorded which then gives the Round-trip time.
No-Operation:
No-operation field is only used for padding, in the above picture it can be seen that the option field is 20 bytes, so it is required to keep the option field to the multiple of 4, that’s why the no-operation field is used.
SACK:
Selective Acknowledgement (SACK) is a mechanism that allows a receiver to acknowledge only the received segments from the sender, If some block of data is not received then that particular block of data is retransmitted not all of the data!
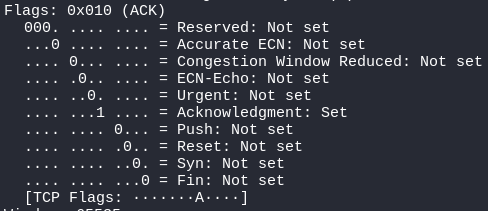
Flags
Flags indicate what type of TCP segment it is or what its purpose of it! 0 bit means the flag is not set if the bit is 1 it means the flag is set, In the below example Acknowledgment bit is set which tells it is an ACK Packet!