Web Application Penetration Testing CTF 1 — Walkthrough
Last updated: July 17, 2025
Hi everyone! In this article, we will solve the Web Application Penetration Testing CTF 1 (eJPTv2). I will not share the flags because I don’t want you to copy and paste them, but rather solve it yourself and follow my instructions, so sit back and read!
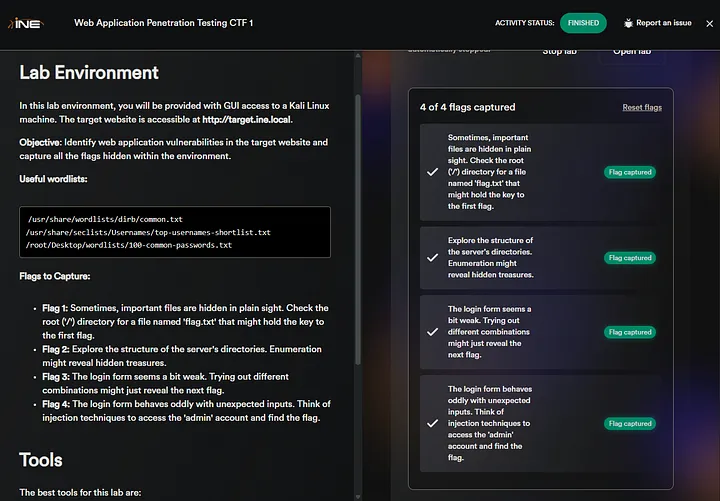
Flag 1: Sometimes, important files are hidden in plain sight. Check the root (‘/’) directory for a file named ‘flag.txt’ that might hold the key to the first flag.
Just head towards your browser and access the web application. You might see an interface like this:
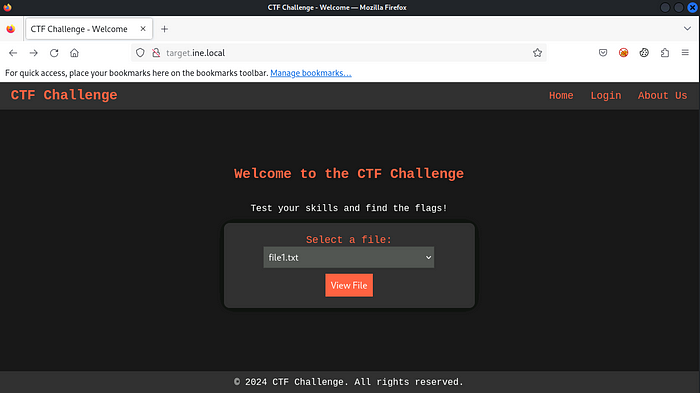
We can select a file to view, so if we select the first file, which is ‘file1.txt’, and view it:
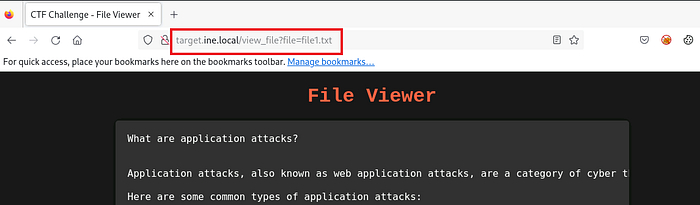
In the URI, it is: /view_file?file=file1.txt, so it’s the API that is calling to view the file1.txt
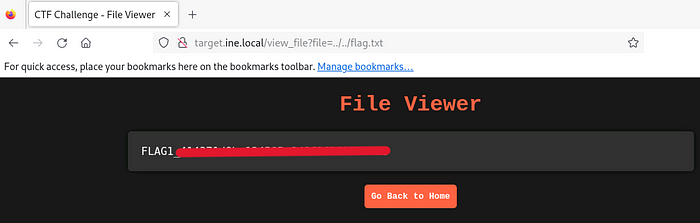
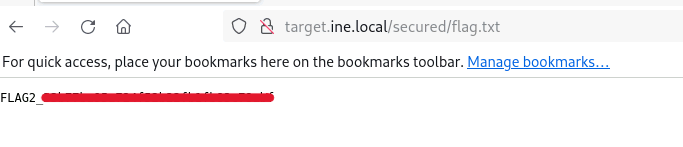
Since the question indicates that the file is located in the root directory, let’s attempt a Local File Inclusion (LFI) attack by modifying the parameter to ../../flag.txt. This successfully retrieves our first flag:
Flag 2: Explore the structure of the server’s directories. Enumeration might reveal hidden treasures.
So the question tells us to explore the structure of the server’s directory. Let’s enumerate it by using the ‘dirb’
dirb http://target.ine.local
It will use the default wordlist
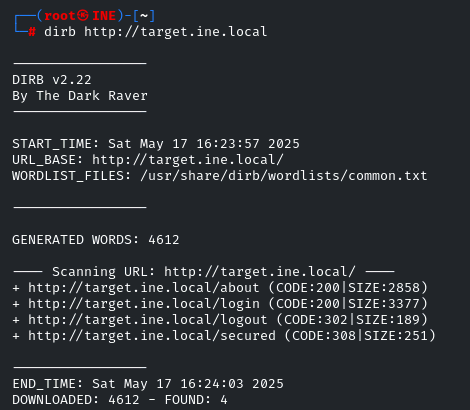
Hmm… /secured directory looks interesting, let’s navigate into it!
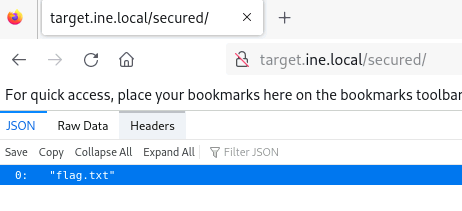
Yes! Inside the /secured directory, there is the file ‘flag.txt’
Just navigate into it and you will get it!
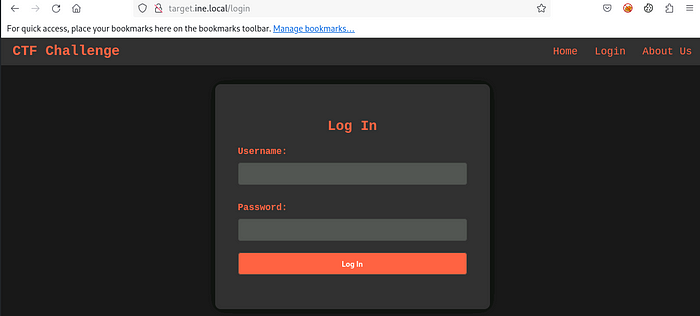
Flag 3: The login form seems a bit weak. Trying out different combinations might just reveal the next flag.
It’s Simple! We have to brute-force the login page 🙂
We can do this by using Hydra
hydra -L /usr/share/seclists/Usernames/top-usernames-shortlist.txt -P /root/Desktop/wordlists/100-common-passwords.txt target.ine.local http-post-form "/login:username=^USER^&password=^PASS^:F=Invalid username or password"
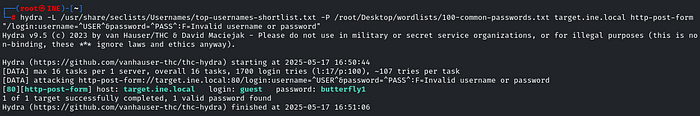
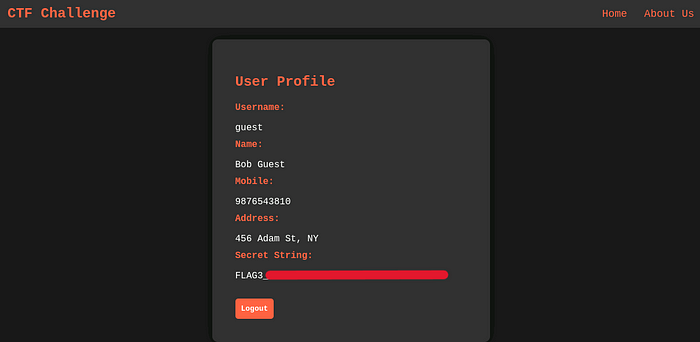
We successfully brute-forced the login page and got the creds
guest:butterfly1
Flag 4: The login form behaves oddly with unexpected inputs. Think of injection techniques to access the ‘admin’ account and find the flag.
Hmm… unexpected inputs and the login page! Let’s try SQL injection
We have to access the admin account, so the username will be the admin
We can try the SQL injection in the username field:
admin' --
And in the password field, you can enter anything!
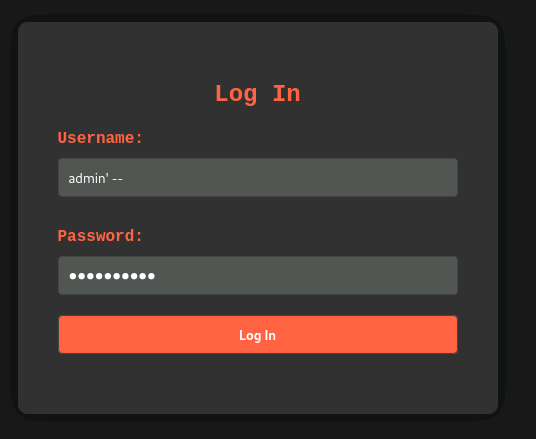
There you go!
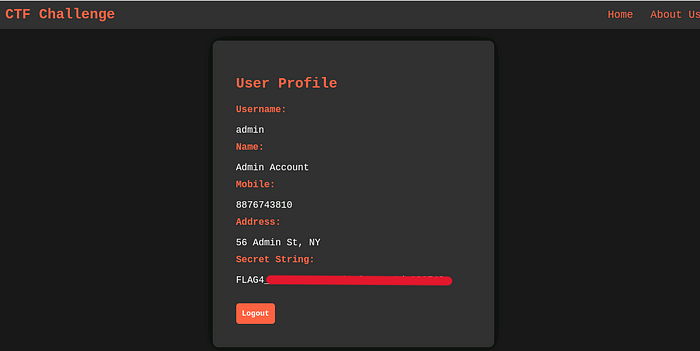
And here all the CTF challenges of the eJPTv2 come to an end. 😊
These challenges covered a wide range of topics, including network enumeration, system exploitation, and web application penetration testing. Each task reinforced practical skills essential for real-world ethical hacking and highlighted common vulnerabilities and attack vectors. This journey serves as a strong foundation for more advanced penetration testing and cybersecurity learning. On to the next challenge! 🚀 See you soon 🙂
